Microsoft 365 Security Assessment Part 2
Last week I shared part one of my Microsoft 365 Security Assessment where we took a deep dive into...


A few months back, we did a short introduction to Advanced Security Management (ASM), a stripped-down version of the Cloud App Security suite, tailored to the needs of Office 365 administrators. As it is now a year since the product was officially launched, I thought it’s a good idea to take it for another spin and compare it to its big brother, in terms of Office 365 related functionalities that is.
User Groups is a new concept, which allows you to scope Alerts and Filters to a subset of users in your organization. Two Automatic groups are created by default, one containing all the users with administrative privileges in your Office 365 tenant and one containing all external users. Apart from the automatically created groups, you can also import user groups from your connected apps. In the case of ASM, only Office 365 is a connected app, so the relevant groups are imported from Azure AD. Once imported, membership of the group is kept in sync. To learn more about user groups, check the documentation here.
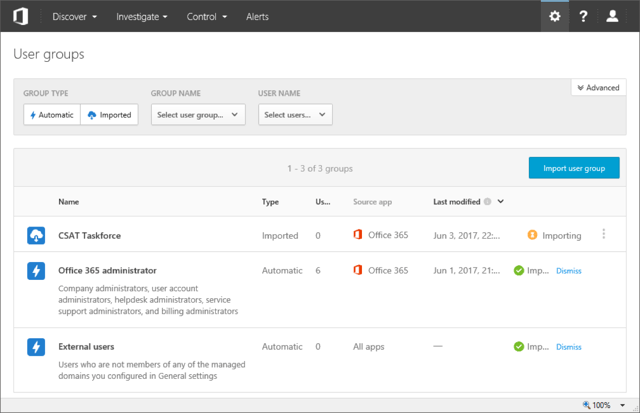
Clicking on a group name will allow you to see its membership, by taking you to the newly introduced Accounts page and filtering the results based on the group id. For some reason, no link to the actual Accounts page is exposed in the Advanced Security Management (ASM) UI, and you have to use workarounds in order to get to it, such as accessing the URL directly (https://tenantname.portal.cloudappsecurity.com/#/accounts). If you are using the full Cloud App Security (CAS) suite, you will find the Accounts link under the Investigate tab.
The accounts page allows you to get a quick overview of the users in your tenant and some of their most important properties, without having to navigate away from the ASM console. The User principal name is used as an identifier, with the icon next to it showing whether the user is internal or external, whereas the small overlay icon indicates admin status. The Apps column lists all applications the user has access to, meaning applications the Cloud App Security suite works with, not all the individual apps within the Office 365 suite for which the user is licensed. In the case of ASM, you will see Office 365 listed, and depending on the licenses, SharePoint Online, OneDrive for Business and the actual ASM app.
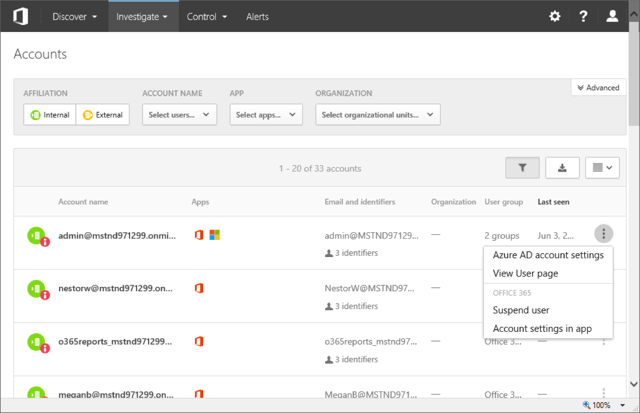
In addition to that, you can get information about some of the user properties, including group membership and last login date. Pressing the menu button on the far right will reveal shortcuts that take you to the settings page for the user in the Azure AD portal, or the corresponding page in the Office 365 Admin portal (via the “Account settings in app” link). A Suspend user quick action is also present. Disappointingly, the User page link is broken as the relevant functionality is not available in ASM. For those using the full CAS suite, the User page has been a useful resource, allowing you to get a comprehensive summary of the user’s properties, activities, files and more. You can learn more about the Accounts page here.
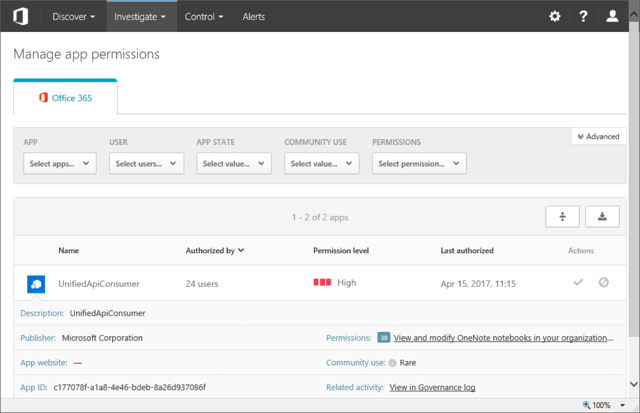
Continuing with the UI changes, the Activity log menu item is now found under the Investigate tab, matching the UI we have in CAS. Under the same tab, the new App permissions menu item is added. Basically, it lists any non-default apps or service principals added to the tenant, along with details on their usage and permission levels. Quick action buttons to Approve or Block the application are provided. Since the same level of detail can easily be obtained via Azure AD PowerShell or the Graph API, I don’t find this new functionality terribly useful (you can get more info about it here).
Another new item in the UI is the Discover tab, the gateway to the Productivity App Discovery feature that is now included as part of Advanced Security Management. By analyzing the network traffic logs captured by the perimeter devices on your network, the Productivity App Discovery features allows you to better understand how your users use cloud applications from different vendors. A huge database of over 14000 cloud apps is used to compare your network data against, revealing potential risks and allowing you to take control over Shadow IT. The full version of this feature, available as part of CAS, allows you to configure automatic log uploads and continuous report generation, exclude users, anonymize data and more. Browsing the comprehensive Cloud app catalog is also only available with CAS.
As the number of events covered by the Office 365 Unified Audit logging increases, so will the number of activity types supported by Advanced Security Management. The list of activity types that will be supported soon includes: Skype for Business activities, Yammer activities, PowerBI activities. Better integration with Azure AD is also on the roadmap, focusing on covering more events such as the signals generated by Azure AD Identity protection. In addition, support for new governance actions is planned, such as resetting a user’s password.
Apart from events availability, some other improvements have been made to alert policies. For example, one can now set an option to only count unique file or folder names when configuring policy with repeated activity filter. When creating an Anomalous activity policy, a new Risk factor is now available, namely the Risky IP Address, which you might be familiar with from the Azure AD Information Protection alerts.
One of the more interesting additions is the new Potential ransomware activity template. Released as a response to the recent WannaCry outbreak, the template preconfigures an alert that detects mass uploads, synchronization events or renames of files and compares the file extension against a list of known file types used by ransomware. While it hardly brings anything new to the table as no new functionality was introduced and can even be considered as marketing stunt, the new template illustrates just how important awareness and (admin) user education is when it comes to even taking advantage of the security features you already pay for.
To access the new “Potential ransomware activity template”, navigate to the Control tab and select Templates, or simply create a new policy and select it from the Policy template dropdown. Additional information about the template can be found here.
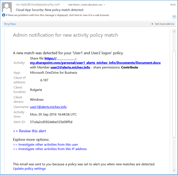
When it comes to Alerts, things haven’t changed much since the last time we looked at them. On the positive side, the signals generated by the Office 365 Unified Audit log are more reliable nowadays, but delays will still occur. Some additional in-context information is now displayed when handling the alert, but the available actions remain the same. Apart from dismissing the alert, resolving it or marking it as unread, you have quick links to editing the parent Alert policy and perform some Governance action on the users involved in the incident at hand.
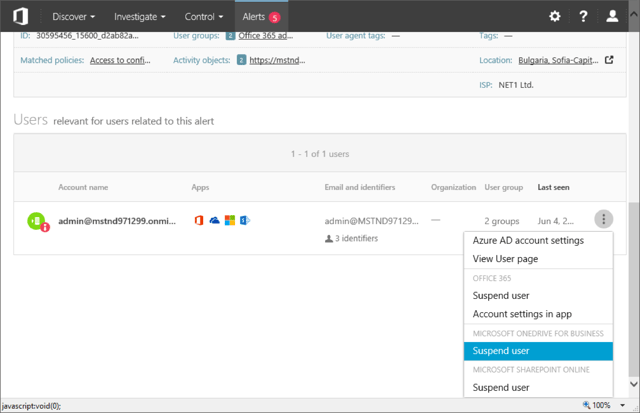
As shown on the above screenshot, in reality the only governance action available is still to Suspend the user, however quick links to the Azure AD portal or the User page in ASM (currently unavailable, see above) are added. What’s more interesting is the addition of SharePoint Online and OneDrive for Business sections, which hint to possible expansion of the available actions in the coming months. To give you an idea what these actions might be, here’s a screenshot of the actions one can use to act upon a match generated by a File policy, as available in the full Cloud App Security suite. To learn more about File policies check this article, and this one to cover all governance actions.
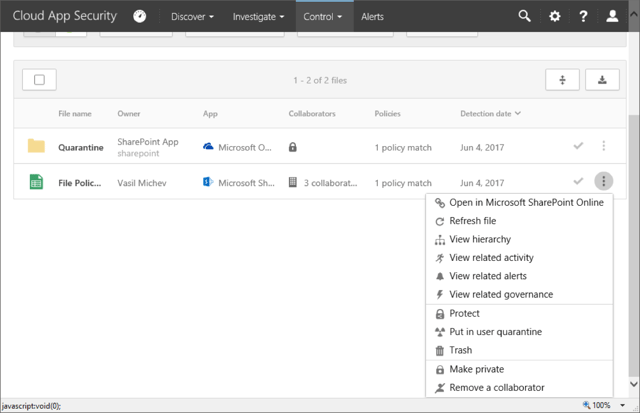
Hopefully, we will get this type of governance actions as part of ASM too. As already mentioned above, an action to reset the user’s password in Azure AD is also coming soon.
Advanced Security Management was released a year ago, which in the world of Office 365 is a long time. While we have seen some polishing of the ASM UI and the addition of new features such as the Productivity App Discovery and App permissions, the pace of improvements has been somewhat disappointing. ASM has been slow to pick up on the new signals available in the Office 365 Unified Audit pipeline, such as Teams related activities, even though they are recognized by both the Security and Compliance Center Audit log search and CAS.
The improvements we’ve seen with the Cloud App Security on the other hand have been more impressive. To name a few: integration with Azure Information Protection, more governance actions for Files, data anonymization for the Productivity App Discovery, “read-only” admin access and more. If you want to take advantage of them however, you have to pay the premium price of 4.2 EUR per user per month for CAS (compared to 2.5 EUR per user per month for ASM), even though you might not care for any of the other functionalities CAS offers, such as managing Box or G Suite.
Considering that ASM was marketed as a stripped-down version of CAS, tailored to the needs of Office 365 customers, it’s hard to understand why some features continue to be only available as part of CAS. Take for example File policies. File policies have been around for a long time, and they certainly add a lot of value for any SharePoint Online or OneDrive for Business customer, yet they haven’t been brought to ASM. The integration with Azure Identity Protection is another similar example.
To end on a positive note, the SIEM integration feature we have available in CAS will be ported to ASM in the coming months. Hopefully other features will soon follow suit.

Vasil has been actively involved with Office 365 for over four years now. He spent over an year as Support Engineer for Microsoft Online Services with one of Microsoft's vendors, working with BPOS and Office 365 customers. Switching sides, he later held support positions with several multinational enterprises, before finally moving to a consultant role. This varied experience allows him to have an unique perspective on the ins and outs of the Office 365 suite. He has closely followed the evolution of Microsoft's cloud offerings, starting with BPOS, with expertise covering all stages of the Office 365 lifecycle. He holds a charter member certification for Office 365 (MCITP and MCSA), and has been awarded as Microsoft MVP for second year in a row.


Last week I shared part one of my Microsoft 365 Security Assessment where we took a deep dive into...

In the previous part of this series, we did a short overview of the Advanced Security Management...