The Hard Part of Soft Matching between Active Directory and Azure AD
One of the pieces of feedback we received from a previous ENow post (integrating your temporary...


In Part 1, I discussed the implication of CFO fraud and how it can affect your company. It can cost a lost of money when transferred to the wrong accounts, CEOs and CFOs get fired and I won’t mention the reputational damage, which can also be substantial. I also discussed the technical part to fight this (i.e. implementing SPF, DKIM and DMARC). This can help you prevent external mail servers trying to spoof your domain and trying to impersonate your users.
What I didn’t mention in the previous blogpost was the use of a solid anti-spam and anti-virus solution. There are several vendors that offer these services, both on-premises and in the cloud, and some are better than others. But for this blogpost, let’s assume we’re using Exchange Online Protection.
Besides the technical aspects, we have to focus on more areas, and the users are part of that.
From a security perspective you want strong passwords, with 16 characters or more, have it changed every 30 days and extremely complex. End-Users have the opposite opinion, it should be easy to remember and preferably never changed. I can understand both.
Last week I received this message in my inbox:
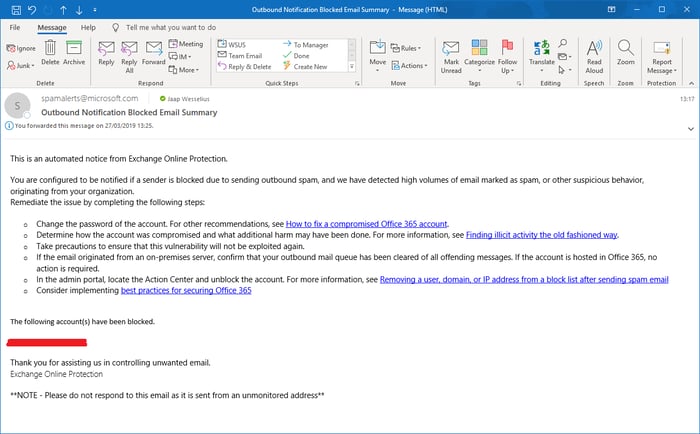
Red flags and alarm bells all over the place, somebody’s account has been compromised and the hacker was sending out spam messages to member of this user’s address book. Thankfully EOP recognizes this and automatically blocks the account and informs the tenant administrators, so we were almost immediately aware something was wrong.
When talking to the user it became clear he was using a simple password, in this case the name of the local soccer club followed by a number. Other examples of weak passwords are Summer2019, NameofyourDog123, Qwerty135 etc. The hacker got access to this account by using a password spray attack, where simple passwords are used against account names in Office 365. Scripts for password spray attacks including user lists and password lists are easy to find on the Internet, so everyone is vulnerable to these kinds of attacks.
In order to prevent weak password usage, Microsoft has the password protection feature. Microsoft has a list of thousands of weak password examples that are used when changing a password. Weak passwords are automatically blocked. Passwords are also normalized, so if you want to use something like Spr!ng2o!9 it is automatically normalized to Spring2019 and again it is blocked. Users might not like this at first, but it is a good measure against password fraud.
Password protection is available in the cloud, but can be combined with the password writeback feature. Passwords are changed in Azure Active Directory (and thus protected by Password protect) and then written back in on-premises Active Directory. Password protection is also available for on-premises Active Directory. An agent is installed on the on-premises Domain Controllers, and when a password is changed in Active Directory, the password is sent to Azure AD, processed by Password protection and when all is ok the password is stored in on-premises Active Directory.
Everybody that has a mailbox has a username and a password, that’s obvious. But despite all security measures, it can be compromised. An additional method of authentication is very useful, so next to your password use your mobile phone for a verification message.
You logon using your regular credentials, a text message with a validation code is sent to your mobile phone and this needs to be entered. If the wrong code is entered you won’t get any access. And, if somebody gets their hands on your password, they still need your mobile phone to get the verification code before they can access your data.
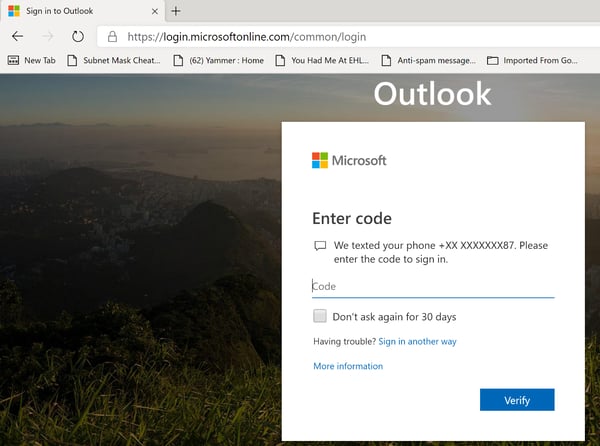
It is possible to configure a grace period, in the screenshot a 30-day period is used. When a code is successfully entered, you don’t need to enter it for the next 30 days. This is per device, so when you want to access your mailbox on another device, the multi-factor authentication needs to be used again. An interesting option when using MFA is “Trusted IPs”. IP addresses of trusted locations like office locations, branch office locations, home office etcetera can be used to bypass the MFA. This way MFA is not used when you are in such a trusted location, but the hacker far away still is facing MFA.
Multi-Factor Authentication for tenant admins is free (and strongly recommended!), a cloud version of MFA is available in all Office 365 business subscriptions. Information on how to implement MFA can be found on my blogpost Implement Azure AD Two-Factor Authentication for users.
The last option I want to mention is regional blocking. The account that I mentioned in the simple password section was compromised from an IP address in Nigeria. My customer is a multi-national with offices and factories in several countries, but not in Nigeria or anywhere in Africa for that matter.
When you have an Azure AD Premium P1 or P2 license, or an Enterprise Mobility + Security (EMS) E3 or E5 license you also have access to Conditional Access with Named Locations. You can define locations based on IP address or countries which are treated as Trusted Location.
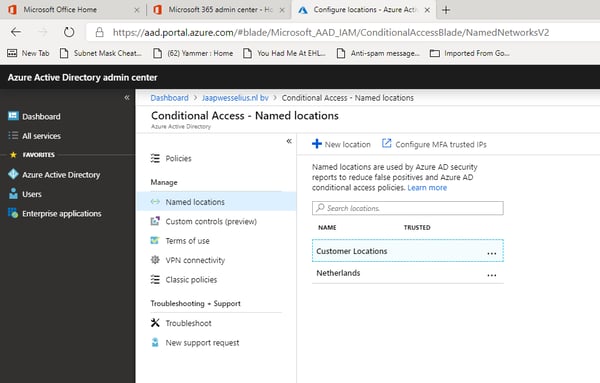
Then you can create a Conditional Access Policy where you define which users, which platforms, which locations and which applications are granted access. Or denied access of course. By using this you can make sure that hackers from countries you don’t have any presence try to get access to your online services.
All solutions I have mentioned in this and the previous blog are technical solutions that can help prevent unwanted access to your services. But you also must take care about your end-users. They also must work with all technical solutions, with all services and they also face all kinds of threats from unknown sources.
Inform your users, train your users to identify phishing messages. There are so many Office 365 look-alike sites on the Internet, and their only purpose is to steal user credentials.
A lot of phishing message appear to come from Microsoft, saying the mailbox is almost of full or temporary locked. If an email says there are 7 voicemail messages waiting. I always ask my customers why they should click if we don't even haven’t any voicemail services. And the fancier an email looks, the more likely it is a phishing message.
At the same time, I must admit that some phishing email are so sophisticated and look so real that it is very hard for an untrained eye to identify as phishing email.
But remember, train your users and make them aware of all hazards that are waiting there on the dark and dangerous fields we call internet.
Besides all network and server related topics that are included in my previous post, you must take care about your own resources as well. Difficult passwords are annoying for users, simple passwords are easy to hack. Use features like password protection, multi-factor authentication or regional blocking to decrease the risk of being a phish victim. Trust me, that’s not what you want to happen.
And next to all technical measures, train your users. Make them aware of potential hazards, tell them about the options you have improve security and help them identify spam.
Proactively monitor AD FS from the end-users perspective with ENow's industry leading monitoring platform. ENow monitors all of your AD FS servers and performs synthetic transactions, including performing a Single-Sign-On against Office 365 from inside your organization and outside (remote tests).

Jaap is a Microsoft MVP for Office Apps and Services. Jaap is an independent consultant, primarily focusing on Exchange server, Skype for Business and Office 365.

One of the pieces of feedback we received from a previous ENow post (integrating your temporary...


Microsoft’s identity portfolio consists of many products, like Active Directory, AD FS, Azure AD...