Zero Trust Networking and Arguing with Physics
When you’re in your own data center and your security model is based on perimeter security and...


At Microsoft Ignite 2019 last year Mark Simos, Lead Architect for the Microsoft Cybersecurity Solution Group, ran a groundbreaking session about the top ten best security practices for Azure today. In his session, he discusses the need for stronger cloud security as more computing environments moving to the cloud. This blog post covers a summary of the session and gives you an overview about the latest Azure security innovations and what’s new in Azure Security Center.
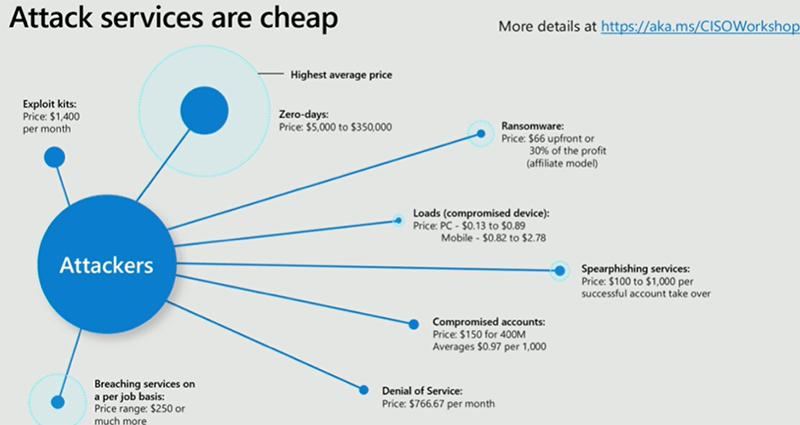
Attackers are using several methods to compromise systems, starting from exploit kits to denial of service over ransomware and phishing. Depending on the purpose an attacker pursues, each attack costs a specific amount of money. The following pictures shows an average application price on the dark web (first-party research from Microsoft).
The Azure Security Compass contains basic information about strategies and threats evolve, the Microsoft security practices and how to transform your cloud journey in a secure manner. The security guidance contains information about governance, risk, compliance, identity, administration, information protection and storage.
There are many presentations, videos and information about basic and advanced security guidance for your needs within your organization. More information can be found at the free Chief Information Security Officer (CISO) Workshop Training from Microsoft.
The Azure secure score reviews your security recommendations and prioritizes them for you. This helps you find the most serious vulnerabilities so you can prioritize investigations. Secure score is built on Azure policy, which itself is built on Azure resource manager (ARM) where Microsoft effectively instrumented all the resource management in Azure. This results in not only visibility on all the things that are allowed or done, but also the ability to control it through Azure policy to block things that you don’t want to happen, for example creating a specific type of resource for certain people within your organization.
With many services offering security benefits, it’s often hard to know what steps to take first to secure and harden your workload. Azure secure score is the first step, no matter if your organization is already in the cloud or is planning the move to the cloud. It helps you to assess your workload security posture and gives recommendations for further analytics.
To protect your accounts, passwords are not enough. They can easily be guessed and compromised, even if you are using a password manager: if the service or database itself is being hacked, your data is not safe anymore. The most common attacks are password spray, phishing, and breach replay.
Another good approach is to use Privileged Identity Management (PIM) for just-in-time access to specific roles. This reduces the time an attacker could get access because your administrative accounts only have specific admin roles if they are really needed.
Admin workstation security like Privileged Access Workstation (PAW) provide a dedicated operation system for sensitive tasks that is protected from Internet attacks and threat vectors. Separate these sensitive tasks and accounts from the daily use workstations and devices provides strong protection.
To secure your network, a best practices is to centralize the management of your core network functions, like ExpressRoute, virtual network and subnet provisioning, and IP addressing. Logically segment subnets is also a good idea to secure your environment. For example, segment a larger address space into subnets, create network access controls between subnets, avoid small virtual networks and subnets to ensure simplicity and flexibility. Zero Trust networks protect corporate data and resources while ensuring that organizations can build a modern workplace. Zero Trust networks eliminate the concept of trust based on network location within a perimeter. Instead, Zero Trust architectures use device and user trust claims (e. g. Conditional Access) to gate access to organizational data and resources.
Threat Protection can be enabled for a lot of Azure resources. This allows you to monitor and analyze potential attacks for your Azure resources and – if required – export or integrate with your SIEM / analytics solutions or Azure Sentinel.
You can integrate security for both development and operations of your cloud applications. Using resources and lessons learned by external organizations that are early adopters of these models can accelerate the improvement of an organization’s security posture with less expenditure of efforts and resources.
It is very important to know and note which person or group of persons made which security decision. As a best practice, designate groups (or individual roles) that will be responsible for key centralized functions.
Identify the new perimeter. Therefore, it is necessary to protect the gateway you get in to use your cloud resources, mostly username and password. In addition, legacy workloads require network protection from internet sources and there are advantages to use Native Azure Controls or 3rd party Network Virtual Appliances (NVAs) for internet edge security.
Web Application Firewalls (WAF) are necessary in today’s world. This is where it does the inspection of the application interaction like the calls to SQL etc., looking for SQL injection and all sorts of fun things like cross site scripting. You can use the built-in functionality called Azure Application Gateway or use 3rd party products.
Backed by the Microsoft global network, DDoS Protection brings DDoS mitigation capacity to every Azure region. Scrub traffic at the Azure network edge before it can impact the availability of the service.
There are two choices for DDos. First, by putting a workload in Azure you get what we call basic DDoS, which means you are on a Microsoft network either it’s Xbox, MSN etc. and Microsoft is protection this network segments for no additional charge. Second, the standard DDoS protection capability is tuned to your apps and you have advanced logging and telemetry data available. This could be used for business-critical applications that needs more granular protection from DDoS attacks.
The Azure platform already filters malformed packets and most classic NIDS/NIPS solutions are typically based on outdated signature-based approaches which are easily evaded by attackers and typically produce high rate of false positives. In Azure, the malformed packets are cleaned at the network edge and they never make it to your services period.
Keeping your resources safe is a joint effort between your cloud provider, Azure, and you, the customer. You have to make sure your workloads and resources are secure. Microsoft provides a lot of different security features, whether you need to protect your Infrastructure as a Service environment like virtual machines, your cloud applications, and other services like SQL, storage, and all the other stuff. But this is not limited to a cloud-only organization, you can protect your hybrid environment with Azure capabilities as well. Security plays an important role and Microsoft spends over $1 billion on cybersecurity each year. You should consider to evaluate which resources needs basic protection available with built-in services and which resources needs more protection and bring this information to your organization.
ENow’s solution is like your own personal outage detector that pertains solely to your environment. ENow’s solution monitors all crucial components including your hybrid servers, the network, and Office 365 from a single pane of glass. Knowing immediately when a problem happens, where the fault lies, and why the issue has occurred, ensures that any outages are detected and solved as quickly as possible.

Dominik is a Microsoft MVP primarily specializing in Microsoft Exchange, Exchange Online and Office 365. Dominik currently works for a German consulting company, AtWork. At atwork, Dominik focuses on designing and building message infrastructures and cloud technologies. Dominik has worked in IT since 2004, primarily with Exchange Server but also has experience with Windows Server, Active Directory, Azure, Office 365, Unified Messaging and various third party products.


When you’re in your own data center and your security model is based on perimeter security and...


Microsoft 365 tenant-to-tenant migrations happen very often. There are merger and acquisitions,...