New ID and Authentication Features
Ignite is Microsoft’s major conference for new announcements and training aimed at IT...

I still remember the first password I ever had; it was for my GeoCities account in the late ‘90s before they were purchased by Yahoo!. The password was a randomly generated string of six lowercase characters – that was it, no uppercase, numbers or special characters. I memorized it and thought it was great, no one would ever guess that random password – unlike the passwords my friends used, which were usually the name of their girlfriend or their nickname. By today’s standards though, it is clear that a lot has changed since then, and I’d be willing to bet that any decent authentication system would actually prevent you from using such a trivial password.
The trouble is, we have more passwords than ever before – almost everything we do today is connected to the internet in some way and requires a set of credentials. For those of us who work in technology, it comes with the territory and over time we’ve become numb to it through the use of password managers and the like. I recently helped my non-technical brother move into a new home and we had to create at least four different accounts in order to manage the smart home products that had been installed by the previous owner. You may be thinking that this all sounds like a consumer problem and many organizations have solved this problem for their end-users by making use of single sign-on (SSO) technologies and you’d be right to a certain extent. SSO doesn’t solve for human behavior though and password reuse has long been a problem. The 2019 Verizon Data Breach Investigations Report(1) found that 80% of hacking-related breaches still involve compromised and weak credentials with 29% of all breaches involving the use of stolen credentials. A quick look at haveibeenpwned.com reveals that it currently has more than nine billion compromised passwords in its database.
In 2004, Bill Gates famously predicted the demise of passwords when he said “There is no doubt that over time, people are going to rely less and less on passwords.” because “they just don't meet the challenge for anything you really want to secure." and while it may have taken 15 years for Bill’s prediction to come true, passwordless authentication is starting to become a reality.
Let me start by telling you what is not - passwordless authentication does not mean that all your user objects will no longer have passwords associated with them, instead it is a type of multi-factor authentication (MFA) that replaces the traditional password with something you have with something you are (biometric) or something you know (pin) provides the second factor. Microsoft currently supports three passwordless authentication options:
In this walk-through, we’ll enable passwordless authentication and configure a FIDO2 Security key for a user called John Smith. For an up to date list of supported FIDO2 Security key providers see this link.
The first step required to deploy passwordless authentication is to enable the ‘Combined security information registration (preview)’ in Azure AD. To do this,
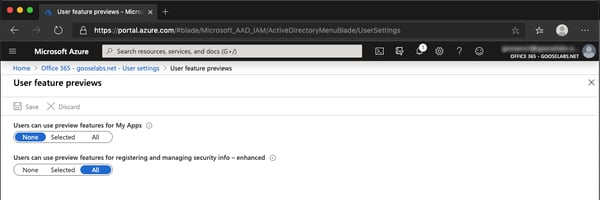
Next, we need to enable the FIDO2 security key method:
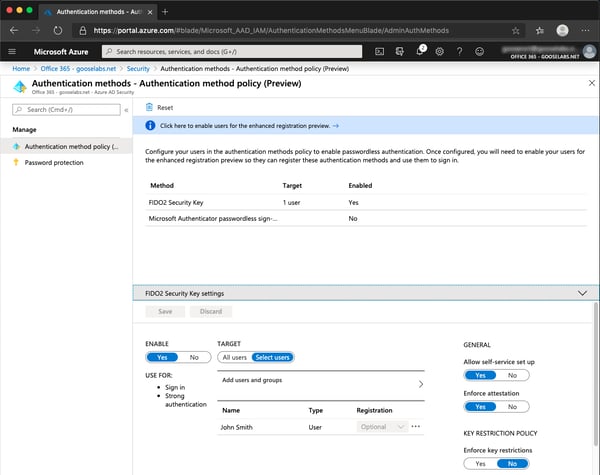
The final step before being able to sign in is user registration. An important note here: If they don’t have at least one MFA method registered, they will need to add one before registering their FIDO2 Security key. To register your FIDO2 Security key:
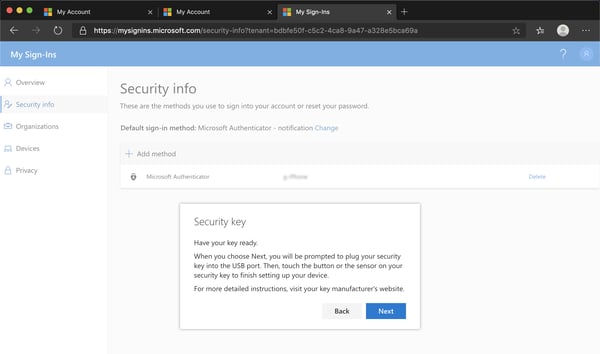
Once user registration has been completed, the sign in process is really simple – instead of entering a password you can select the ‘Sign in with a security key’ option as shown in the brief demo below:
As you can see from the walk-through above, getting started with passwordless authentication in Azure AD is really simple, however, it should go without saying that doing this in a large organization would require careful planning and thought.
ENow’s Office 365 Monitoring solution is like your own personal outage detector that pertains solely to your environment. ENow’s solution monitors all crucial components including your hybrid servers, the network, and Office 365 from a single pane of glass. Knowing immediately when a problem happens, where the fault lies, and why the issue has occurred, ensures that any outages are detected and solved as quickly as possible.

Office 365 MVP, Exchange MCM, Technology Consultant

Ignite is Microsoft’s major conference for new announcements and training aimed at IT...

Securing your data in Office 365 can be a challenging task. The problem is that using user names...