New ID and Authentication Features
Ignite is Microsoft’s major conference for new announcements and training aimed at IT...


What a great time to be an IT pro. I mean really, who has it better than us? On any given day there is so much going on, so much to learn, so much to improve, and that's why I do really enjoy my job(s). As I think about how to open this blog post, it occurs to me that I’ve had some great opportunities in my career. Sort of a “as one door closes, another one opens” sort of thing.
I have spent most of my career as an “email guy”. I started as a Banyan Vines administrator, moved through numerous evolutions of the email concept, and now I find myself at a place where email is being deemphasized. I don’t mean to say email is “done”. I don’t buy into that nonsense that Yammer, Slack, Teams, Skype, or any other alternative collaboration platform is ever going to replace "email". Email provides a platform that none of those others can replace. Those other platforms can add-on and improve the overall enterprise collaboration experience, but I don’t see "replacing email" as an option that will ever happen.
But I digress. This blog post is about authentication.
I’m coming to a point in my career where I think authentication is the frontier for learning and expanding my capabilities. I think authentication is the lynch pin of the new enterprise. I think authentication is where it all starts. And here's how I like to think about authentication as I start a new migration project.
I handle several different project types these days. Exchange migration projects are still a significant part of overall workload, but I am finding more and more that the actual mailbox migration portion of those projects is less and less an area of concern for me and my customers.
The process of moving mailboxes into and within Exchange Online has become close to rote at this point. In my experience the work that needs to be done is around how to secure that data within Office 365 while ensuring that the end-users who need to access that data can do so quickly and easily.
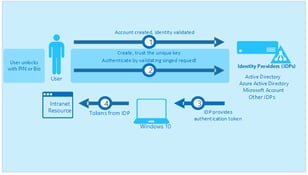
For me, all these projects need to start with the source of authority for user accounts. Today, most enterprise organizations have multiple layers of authentication and user management tools. There are many different places that an IT staff can end up managing user accounts, and in my some-what-less-than-humble-opinion it’s important to identify and codify a single source of authority as the center of every enterprise’s authentication strategy.
For most enterprise organizations, the single source of authority needs to be Active Directory. Deploying and maintaining a strong, healthy, well-organized Active Directory is a vital step that is surprisingly easy to overlook. The great strength of Active Directory is that it’s very easy and very flexible to configure and maintain. It’s also important to point out that this strength is also Active Directory’s greatest weakness. Active Directory is so easy to deploy and so forgiving that it can be very easy to make a mess of your AD forest. I find it vitally important to take the time to review Active Directory and ensure it is in good working order. I know it can be a terrible hassle to ensure that everyone has all their phone numbers, addresses, offices, managers, and other information entered properly into Active Directory but as we expand our authentication options these “extra” bits of information can be important to making our end-user experience the best it can be.
Once we have a healthy and well-organized Active Directory, the next step is to define our requirements. Who should be able to access what data when, where, and on what devices? I find it best to encourage customers to give me a dream scenario with no consideration for what is possible. I find that limiting ourselves (me included) to what we “know” is possible with the current state of technology can lead us to overlooking new configurations and possibilities that have become available.
It’s hard to define this process in a way that works consistently. I like to just ask a series of questions about the different groups of users and how the customer envisions resolving the authentication management problems that group of users. Maybe the customer needs to ensure that only authorized devices are used to access organizational data. Maybe the customer needs to ensure that groups of users are only able to access data from specific locations. Whatever the requirement, I find it helpful to lay them out and get them documented early in the process. A good set of requirements can go a long way to ensuring a project that everyone is happy with in the end.
Once the source of authority is established and clean, and the project requirements are clearly documented, we can start the actual work of designing a solution. For me, designing a good authentication solution is always about finding the tools that meet requirements laid out by the customer. Far too often I do projects where the tools have already been decided on before the project starts and I need to find a way to change the requirements to meet the options. I think the main problem is the sales cycle tends to focus on selling specific products and services to a specific budget. I understand sales cycles and budgets are important, but it’s also important to fit the tools to the organization’s requirements. Although I don’t have a solution for you, it's enough to point out the problem now and encourage you to keep it in mind.
This ended up being more of a blog post about the process of defining an authentication solution than a technical blog about how a new authentication solution works. I’m fine with that, and I think it’s important to consider the process before we consider the technical solutions.
Hopefully you’ve found something you can take away from this blog to make your next project go a bit more smoothly.
Active Directory is the foundation of your network, and the structure that controls access to the most critical resources in your organization. The ENow Active Directory Monitoring and Reporting tool uncovers cracks in your Active Directory that can cause a security breach or poor end-user experience and enables you to quickly identify and remove users that have inappropriate access to privileged groups (Schema Admins, Domain Administrators). While ENow is not an auditing software, our reports reduce the amount of work required to cover HIPAA, SOX, and other compliance audits.
Access your FREE 14-day trial to accelerate your security awareness and simplify your compliance audits. Includes entire library of reports.

Nathan is a five time former Microsoft MVP and he specializes in Exchange, Microsoft 365, Active Directory, and cloud identity and security.

Ignite is Microsoft’s major conference for new announcements and training aimed at IT...


One of the most important aspects of moving to a cloud solution like Office 365 is to provide a way...