How Microsoft Improved Its Identity Products and Services - September 2022
Microsoft’s identity portfolio consists of many products, like Active Directory, AD FS, Azure AD...


Microsoft’s identity portfolio is huge and includes products and services like Active Directory, AD FS, Azure AD Connect, Defender for Identity, Microsoft Identity Manager and Azure AD. Contrary to what some belief, Active Directory on-premises is supported, alive and kicking and here to stay for most organizations. This became abundantly clear in August 2022, as Microsoft improved things for Identity admins in the following ways:
On Tuesday, August 9, 2022, Microsoft issued updates to address 121 vulnerabilities in its products. Microsoft refers to these updates at the ‘8B’ updates. With these updates, Microsoft addressed vulnerabilities in products that are typically managed by Identity admins:
During Patch Tuesday, Microsoft also addressed two Identity-related vulnerabilities in Windows Hello (CVE-2022-35797) and Kerberos (CVE-2022-35756), but these vulnerabilities typically require patching at the client-level and on member servers.
When Domain Controllers are virtualized on top of Hyper-V, two Hyper-V vulnerabilities might make these virtual domain controllers vulnerable when other Windows installations also run on the same virtualization hosts. CVE-2022-34696 and CVE-2022-35751 describe the two vulnerabilities that should be addressed in this case. Other vulnerabilities, such as two vulnerabilities in the Print Spooler service can be ignored when Identity admins have already disabled the Print Spooler service on Domain Controllers, per our earlier advice.
Our advice is to install the August 2022 cumulative updates to Domain Controllers and Certification Authorities (CAs) as soon as possible. A known issue that emerged since the release of these updates is that IE mode tabs in Microsoft Edge might stop responding when a site displays a modal dialog box. For Domain Controllers and CAs this shouldn’t typically be a problem.
With its August 16, 2022, and August 23, 2022, Preview updates, Microsoft addressed a couple of issues that may have already driven some Active Directory admins mad. These updates for Window Server 2019 and Windows Server 2022 address unexpected restarts on read-only Domain Controllers and an issue with token leaks.
These Preview updates, commonly referred to as the ‘8C’ updates, also require printers and scanners that use smartcard authentication to have firmware that complies with section 3.2.1 or RFC 4556. If printers don’t comply, printing stops working.
The 2.187 release of Defender for Identity that Microsoft released on August 18, 2022, improves the logic of the Suspected DCSync attack alert. In previous versions of Defender for Identity, NAT devices would typically falsely trigger this alert.
Network Address Translation (NAT) is typically used to enable a local area network (LAN) to use one set of IPv4 addresses for traffic within that network and another (set of) IPv4 address(es) for traffic that goes outside the network. Within networks, it can be used to segment networks and have entire networks appear as one host. No host can be reached or singled out unless specifically allowed through the NAT setup.
DCSync attacks consist of certain traffic flows towards Domain Controllers. When a lot of traffic appears from one host, while the traffic originates from multiple hosts behind a NAT device, DCSync attacks may be falsely suspected.
Now, cases where source IP addresses seen by the Defender for Identity sensors on Domain Controllers appear to be NAT devices are covered.
AD FS gained two new features in August 2022. The Azure MFA Adapter that is included since AD FS on Windows Server 2016 gained the functionality to work with alternate login IDs.
In addition, Microsoft introduced the new settings in Azure AD. The federatedIdpMfaBehavior setting can be used to specifically require people to perform multi-factor authentication with their organization’s AD FS implementation or specifically ignore any multi-factor authentication done there and require it from Azure MFA.
Speaking of Azure AD… Microsoft labeled some nice new features as generally available (GA) in August 2022.
Organizations can now require a fresh authentication each time a person performs a certain action. Forced reauthentication supports requiring a person to reauthenticate during Intune device enrollment, password change for risky users, and for risky sign-ins.
This brings us one step closer to step up multi-factor authentication whenever an organization requires it to verify the identity of a person. Microsoft is already experimenting with this feature with all personal accounts (previously known as Microsoft accounts, or MSAs) and the Personal Vault functionality in OneDrive for Business.
On August 30, 2022, Microsoft released version 8.1.1.1 of Azure MFA Server. This version introduces a Migration Utility to synchronize multi-factor authentication (MFA) registrations stored in the on-premises Azure MFA Server directly to Azure MFA:
Figure 1The Multi-Factor Authentication Server Migration Utility
After the data is migrated to Azure AD, people can perform cloud-based MFA seamlessly without having to register again or confirm authentication methods.
As Microsoft introduced extensions to the Staged Rollout functionality to include the Azure multifactor authentication (Preview) toggle:
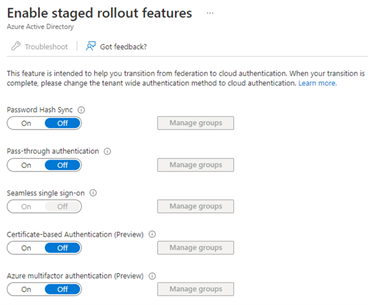
Figure 2 Staged rollout features
When user accounts are added to a group that is enabled for this feature, their multi-factor authentication requests towards Azure AD, Azure AD integrated applications and Microsoft 365 services are handled by Azure MFA instead of the on-premises Azure MFA Server. This allows for a granular migration path. Admins do not need to switch over their entire organization at once but can do so per user account by adding them to the group that is enabled through the toggle.
A commonly overheard phrase these days is “You can’t have Zero Trust when you have AD FS.” While this is a bold thing to say, there is truth to it. Based on it, many admins try to get rid of AD FS. Even though Microsoft offers great resources to migrate applications, systems, and services with relying party trusts (RPTs) to AD FS toward Azure AD, there are scenarios where AD FS is the only Microsoft solution that offers single sign-on.
One of these scenarios was cracked last month, as Azure Virtual Desktop (AVD) no offers Single Sign-on (SSO) without requiring Active Directory Federation Services (AD FS). When all persons that sign in to Azure Virtual Desktops are synchronized users, synchronized through Azure AD Connect, Hybrid Cloud Trust is enabled and the Windows 11 22H2 Preview image is used as the AVD Operating System, single sign-on works. People will only have to authenticate once to access the portal and can than sign in to published resources seamlessly. In addition, people can now use FIDO2 keys and Windows Hello for Business (WHfB) to sign in to the AVD portal.
There are many ways to sign in and pass identity verification in Microsoft’s products and services. Last month’s updates included almost all.
From a 30,000 feet view, we can see how Microsoft adds functionality to migrate more and more on-premises Identity functionality to Azure Active Directory. Take advantage of it, when managing on-premises infrastructure to minimize its use towards the cloud. At the same time, don’t forget to patch those Domain Controllers, AD FS servers and Certification Authorities (CAs)!
Active Directory is the foundation of your network, and the structure that controls access to the most critical resources in your organization. The ENow Active Directory Monitoring and Reporting tool uncovers cracks in your Active Directory that can cause a security breach or poor end-user experience and enables you to quickly identify and remove users that have inappropriate access to privileged groups (Schema Admins, Domain Administrators). While ENow is not an auditing software, our reports reduce the amount of work required to cover HIPAA, SOX, and other compliance audits.
Access your FREE 14-day trial to accelerate your security awareness and simplify your compliance audits. Includes entire library of reports.

Sander's qualities extend beyond the typical triple-A stories in the area of Identity and Access Management. Of course, authentication, authorization and auditing are necessities but my out of the box solutions get the most out of software, hardware and the cloud. Rapid technological advancements have resulted in cutting-edge solutions around Active Directory, Azure Active Directory and Identity Management. Keeping up with these is just a small challenge, compared to my true goal: helping people use the technology on a daily basis. In a way that ICT is not a mere hurdle, but an infinite enabler. His work as a consultant, blogger and trainer are all means to achieve this goal. His multiple Microsoft Most Valuable Professional (MVP) status, Veeam Vanguard status and extensive certification aids him. Through direct communications with the product teams in Redmond, he remains up to date, exchanges feedback and accelerates support. Sander is also a Virtual Product Owner for AppGov and ENow.


Microsoft’s identity portfolio consists of many products, like Active Directory, AD FS, Azure AD...


Active Directory, AD CS, Azure AD Connect, and Azure MFA Server are all Microsoft on-premises...