Azure Active Directory Password Protection
Recently I had to upgrade my Azure AD Connect server from version 1.x to version 2.x, and I blogged...


Previously, MVP Nicolas Blank wrote an interesting article "Having an Identity Crisis" and it talked about all kinds of attacks on your environment. One such attack is on user email. Users tend to choose a password that is easy for them to remember and this makes the password weak and easy to guess by others. Even with some social engineering, user passwords are easy to retrieve, as can be seen on this YouTube clip What is your password?
The question is how to protect passwords? In Active Directory it is possible to enforce complex passwords, but from an Active Directory point of view “Password123” is complex and so is “Summer2020”. Enforcing a password length of let's say 20 characters should help, or so one might think, but the result is that users write down their complex passwords on sticky notes and post these notes in plain sight. That’s not a good idea either.
Azure Active Directory does a better job since it offers something like Password protection. If a user tries to change the password to something that’s easy to guess (I have tried ‘Summer2020’) an error is raised:
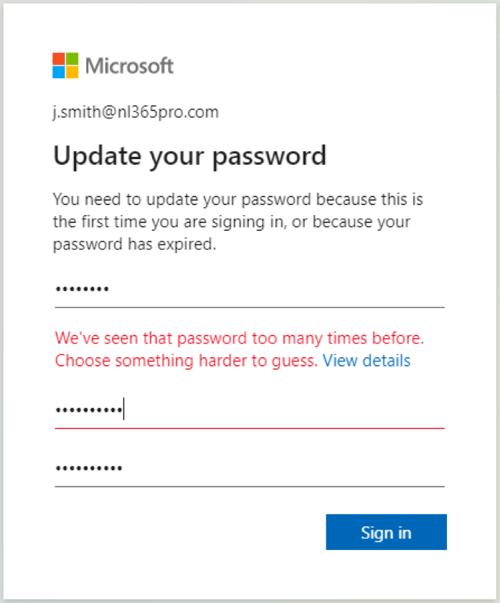
The Password protection feature is available in Azure Active Directory. For online users the basic functionality is covered in the Azure AD free license, for synchronized users an Azure AD Premium P1 or P2 license is required.
To access the password protection feature, open the Azure portal (portal.azure.com) and navigate to Azure AD | Security | Authentication Methods. There’s not much to configure, the password protection feature is pre-configured. There’s a basic list of banned passwords inside Azure AD (which is kept secret by Microsoft for obvious reasons) but there’s also a custom list that can be used. Here you can enter your own banned passwords (max 100 entries).
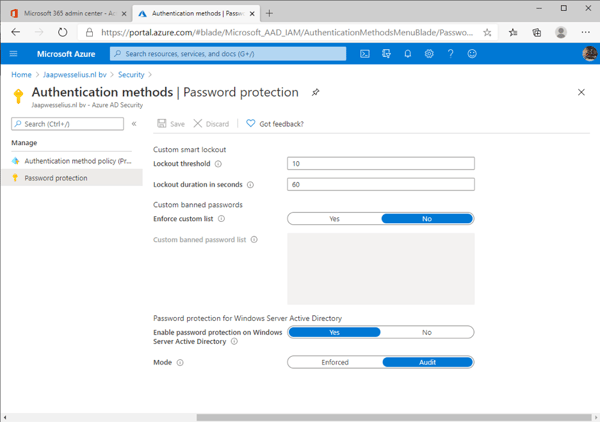
Note. The password protection feature normalizes passwords. So Password01, P@ssword01, Passw0rd01 or Password0! are all treated similar and thus banned.
The password protection feature is only available for Azure Active Directory, but Microsoft offers a proxy solution for on-premises Active Directory. Using an agent and a proxy service on-premises, the password policy is downloaded on-premises when a user changes a password. This way a password change can have a password policy applied the same way as in Azure Active Directory.
Please note that the actual new password is not sent to Azure AD, but a request for the password policy is sent to Azure AD. The password policy is then cached on the Domain Controllers and used to protect on-premises password changes.
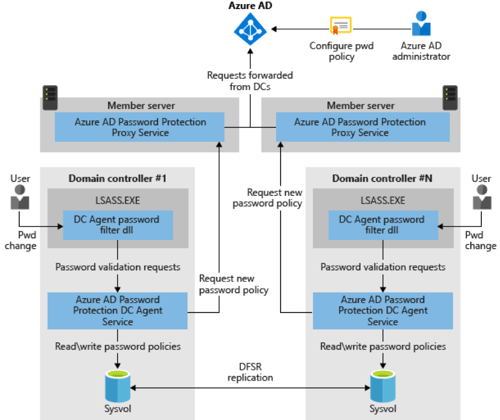
Installation of the password protection services consist of two steps:
Both can be downloaded from the Microsoft download center on https://www.microsoft.com/en-us/download/details.aspx?id=57071
During installation and configuration (two PowerShell commands) a Service Connection Point (SCP) is created in Active Directory so that the Domain Controllers know where the proxies are located.
Now when a user on-premises tries to change the password and uses a weak password (like Password01, Summer2020 etc) the change is not accepted and a warning is shown:
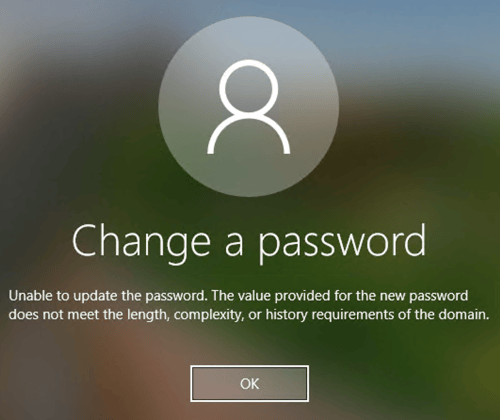
User passwords are always challenging. From a security perspective, complex and difficult passwords are preferred. But users want their passwords to be easy to remember. Active Directory does not offer much options here, but Azure AD does offer a password protection service.
In late 2019 the password protection service became available for on-premises Active Directory as well. The password policies in Azure AD are retrieved by the proxy agents and cached on the Domain Controllers where they are applied. This way users can no longer create passwords that are too easy to guess.
Active Directory is the foundation of your network, and the structure that controls access to the most critical resources in your organization. The ENow Active Directory Monitoring and Reporting tool uncovers cracks in your Active Directory that can cause a security breach or poor end-user experience and enables you to quickly identify and remove users that have inappropriate access to privileged groups (Schema Admins, Domain Administrators). While ENow is not an auditing software, our reports reduce the amount of work required to cover HIPAA, SOX, and other compliance audits.
Access your FREE 14-day trial to accelerate your security awareness and simplify your compliance audits. Includes entire library of reports.

Jaap is a Microsoft MVP for Office Apps and Services. Jaap is an independent consultant, primarily focusing on Exchange server, Skype for Business and Office 365.


Recently I had to upgrade my Azure AD Connect server from version 1.x to version 2.x, and I blogged...


Microsoft’s own integrated STS in Windows Server named AD FS (Active Directory Federation Service)...