Microsoft 365 Security Assessment Part 1
As a Microsoft 365 certified Security Administrator, and Microsoft certified Azure Security Engineer


Last week I shared part one of my Microsoft 365 Security Assessment where we took a deep dive into securing things related to Azure Active Directory. If you haven’t had a chance to read through it yet, take a few minutes and read it here.
Now that we’re all on the same page, lets dive into part two, where we’ll cover security settings in the Microsoft 365 Admin Center.
Modern authentication is what allows you to enforce MFA and other identity based security features. Products that don’t use “modern authentication” use what we call “Legacy Authentication” (obviously) or “Basic Authentication”. It only uses username and password pairs to authenticate a user. The example shown in Figure 14: Basic authentication prompt is using legacy authentication, also known as basic authentication.
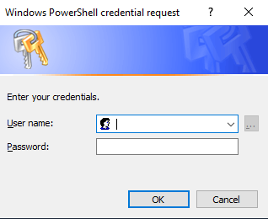 Figure 14: Basic authentication prompt
Figure 14: Basic authentication prompt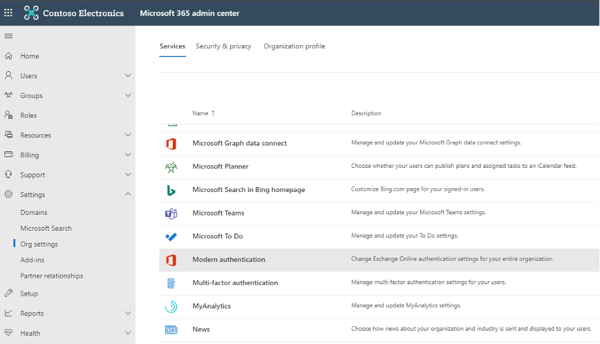 Figure 15: Modern authentication in Microsoft 365 admin center
Figure 15: Modern authentication in Microsoft 365 admin center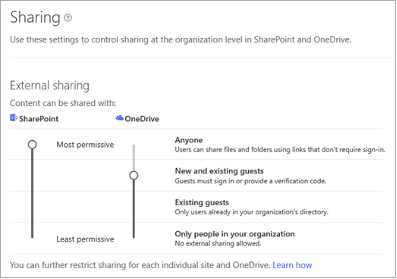 Figure 16: External Sharing settings
Figure 16: External Sharing settings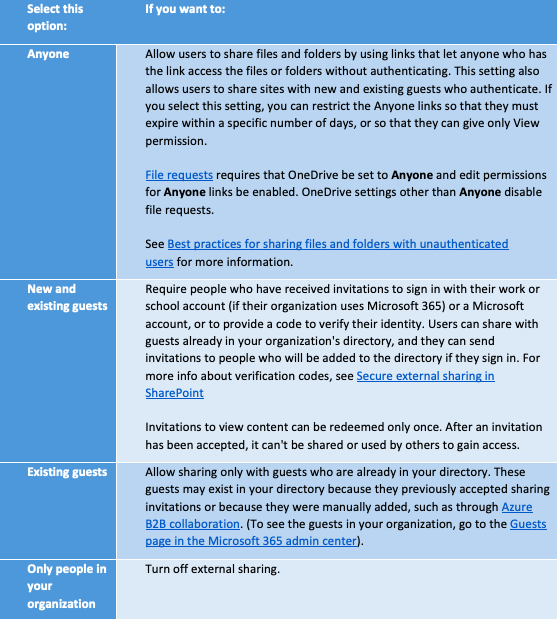
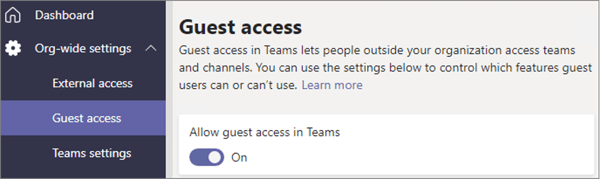 Figure 17: Guest access in Teams admin center
Figure 17: Guest access in Teams admin center
Microsoft Secure Score is a measurement of your organization’s security posture, with a higher number indicating more improvement actions taken. It can be found at https://security.microsoft.com/securescore or in the Microsoft 365 security center.
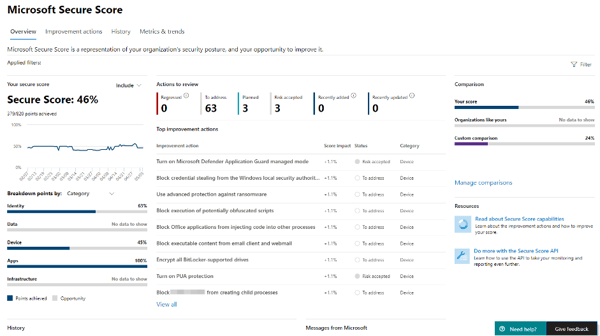 Figure 18: Microsoft Secure Score Dashboard
Figure 18: Microsoft Secure Score Dashboard
The improvement actions are security recommendations that are based on the information pertaining only to your tenant and the settings configured (or not configured). Improvement actions are ranked by implementation difficulty, user impact and number of points achievable. Review the improvement actions, create an action plan to address the recommendations and track your Secure score on a regular basis.
This advice may be obvious to many organizations, but the more privileged accounts you have (accounts with admin privileges to services and data), the easier it is for attackers to target your organization and gain access to data.
It goes without saying that you shouldn’t assign admin roles to user accounts and in fact I recommend that admin accounts do not get assigned a license in Microsoft 365 unless the role requires an email alias.
Assign the least permissive roles to admins and have less than five global administrators (but more than one for emergencies).
“Roles” in the Microsoft 365 admin center (Figure 19: Roles in Microsoft 365 Admin Center) allows you to export the roles and users assigned these roles to a CSV file. Review the list in the export and try to follow the best practices mentioned above by removing some roles from people that don’t need the role and changing the combination of roles assigned to users so they can perform their daily admin function with the least privilege required.
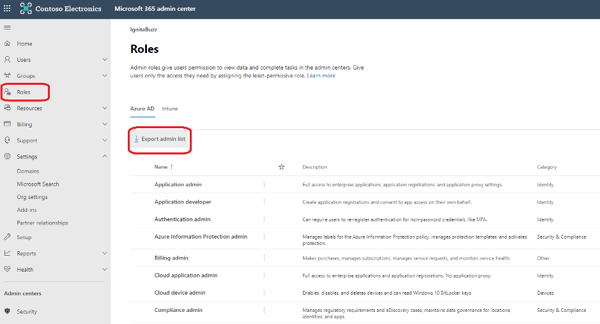 Figure 19: Roles in Microsoft 365 Admin Center
Figure 19: Roles in Microsoft 365 Admin Center
Now, Zero Trust or ZT as I have seen it abbreviated before, is a framework. It’s not something you can turn on in an admin center and “poof” – magic, you are more secure. It is a journey that organizations embark on and strive to improve and enhance in an ongoing fashion.
Zero Trust teaches us to “never trust, always verify.”
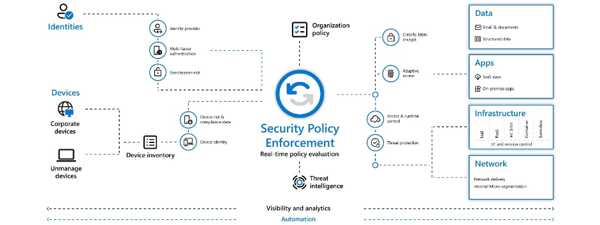 Figure 20: Zero Trust diagram
Figure 20: Zero Trust diagram
There are many resources to help you get started with the zero trust journey. Microsoft have a Zero Trust assessment tool - Take the Zero Trust Assessment (microsoft.com) and Microsoft have also just announced the Zero Trust Deployment Center – a repository of information to improve ZT readiness and implementation guidance.
Configure Microsoft Defender for Office 365.
Defender for Office 365 (previously called Office 365 Advanced Threat Protection) helps you secure your organization by offering a comprehensive slate of prevention, detection, investigation and hunting, response and remediation, awareness and training, and secure posture features.
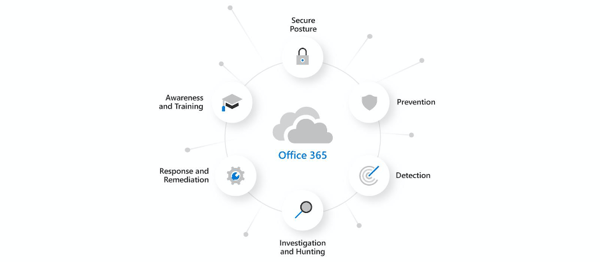 Figure 21: Microsoft Defender for Office 365 components
Figure 21: Microsoft Defender for Office 365 components
Microsoft Defender for Office 365 includes:
- Threat protection policies
- Reports to monitor threat protection in real-time
- Threat investigation and response capabilities to help you investigate, understand, simulate and prevent threats
- Time saving automation for response actions
ORCA (Office 365 ATP Recommended Configuration Analyzer) is a PowerShell report to help validate your anti-spam and anti-malware settings against recommendations from Microsoft. The tool compares your settings to the recommended practices in “Recommended settings for EOP and Office 365 ATP security”
Running ORCA is simple. Install the module, start a PowerShell session logged in with an administrator account and run the Get-ORCAReport cmdlet.
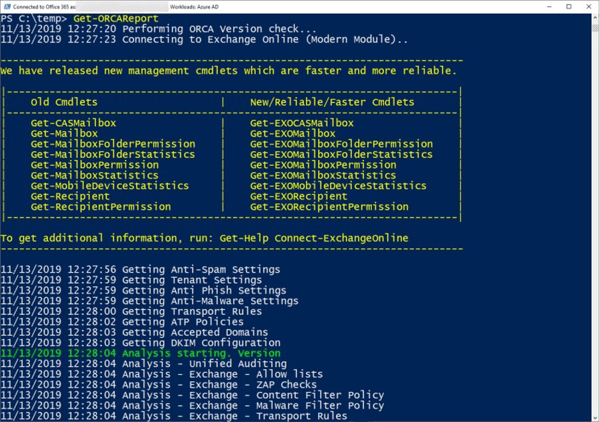 Figure 22: Running the Orca cmdlet
Figure 22: Running the Orca cmdlet
This checklist is not an exhaustive security checklist, but it’s definitely a baseline set of configurations I recommend to most organizations looking to tighten up their security or those that are just getting started with Microsoft 365. If you are new to Microsoft 365 security, it can be a daunting task securing your environment. I hope this list helps you get started because doing something is more secure than doing nothing at all.
Active Directory is the foundation of your network, and the structure that controls access to the most critical resources in your organization. The ENow Active Directory Monitoring and Reporting tool uncovers cracks in your Active Directory that can cause a security breach or poor end-user experience and enables you to quickly identify and remove users that have inappropriate access to privileged groups (Schema Admins, Domain Administrators). While ENow is not an auditing software, our reports reduce the amount of work required to cover HIPAA, SOX, and other compliance audits.
Access your FREE 14-day trial to accelerate your security awareness and simplify your compliance audits. Includes entire library of reports.

Microsoft Security MVP | Principal Architect @NBConsult | Speaker | Blogger. I am an Identity and Access Solutions Architect for NBConsult, a leading IT service provider in South Africa. I have 20+ years of experience in Microsoft enterprise technologies. I am passionate about Identity Governance and how it can help organizations achieve better security, compliance and productivity. I write blogs where I share my insights and tips on Application Governance.


As a Microsoft 365 certified Security Administrator, and Microsoft certified Azure Security Engineer