Identity and Authentication Management for Office 365
The good people at ENow asked me to do a webinar on Identity and Authentication Management for...


Microsoft Ignite was held on October 12 to 14th 2022, and was a truly hybrid event, with in-person sessions held at the Seattle conference center as well as pre-recorded content and Teams live-event style sessions being streamed around the world. The big catch phrase of the conference this year was “Do more with less”. As organizations adapt to new challenges, they are looking to have more choice in the way they work and to get better results with less friction. The updates to products revealed at Microsoft Ignite were aimed at helping customers get the full value of Microsoft’s technologies.
For identity, "doing more with less” means being more efficient by automating IT repetitive tasks and letting machine learning handle basic decisions, while security professionals handle exceptions.
Microsoft Entra, which was announced in March 2022 is Microsoft’s modern Identity and Access admin center.
Since first generally available, the Entra family includes:

Figure 1 Core Entra capabilities (image source: microsoft.com)
With the current identity related threats, identity governance is critical. Identity governance means onboarding and offboarding users, granting access to resources at the right time and just enough access. It also means revoking access when no longer needed.
Identity governance features have already been built into Azure AD. Under the new Entra brand however, Microsoft are building a new complete cloud identity governance product called Microsoft Entra Identity Governance. https://aka.ms/entra/identitygovernance
Microsoft Entra Identity Governance will help organizations simplify operations, support regulatory compliance and consolidate multiple identity point solutions.
Identity Governance already includes:
The newly released capabilities include lifecycle workflows to automate repetitive tasks, connection to on-premises to enable consistent policies for all users and separation of duties in entitlements management to help safeguard against compliance issues.
Lifecycle workflows allows you to create custom workflows that automate onboarding and offboarding tasks so as to manage your users' lifecycle at scale.
Workflows contain specific processes, which run automatically against users as they move through their life cycle. Workflows are made up of Tasks and Execution conditions.
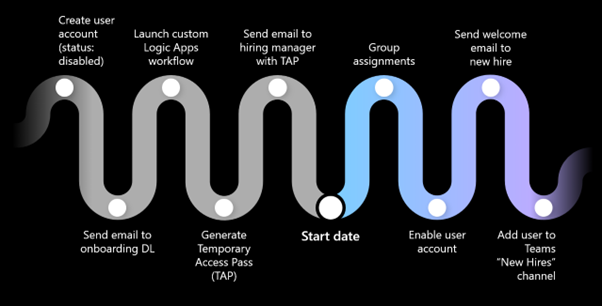
Figure 2 Some of the user identity lifecycle tasks that can be automated (image source: microsoft.com)
Workflows can be created and customized for common scenarios using templates, or you can build a workflow from scratch using Microsoft Graph.
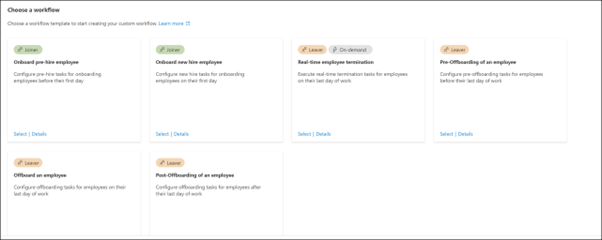
Figure 3 Lifecyle workflow templates (image source: microsoft.com)
Lifecycle Workflows now in Public Preview requires Azure AD Premium P2 licenses.
With the separation of duties settings on an access package, you can configure that a user who is a member of a group or who already has an assignment to one access package can't request an additional access package.
Separation of duties and Entitlement management also supports Microsoft Identity Manager (MIM) and other on-premises identity management systems.
Seperation of Duties (access reviews) is now generally available and rerequires Azure AD Premium P2 licenses
Humans are not the only identities, a workload identity is an identity used by a software workload (such as an application, service, script, or container) to authenticate and access other services and resources. In Azure AD, workload identities are applications, service principals, and managed identities.
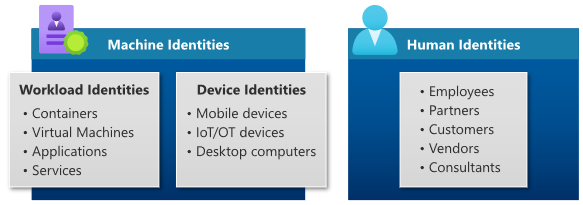
Figure 4 Machine identities vs human identities (image source: microsoft.com)
In recent studies, Microsoft discovered that 68% of workload identities have access to sensitive data and assets, attackers who compromise workload identities can move laterally inside an environment.
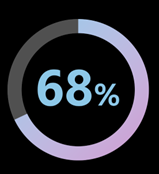
Figure 5 Percentage of workload identities have access to sensitive data (image source: microsoft.com)
The ratio of workload identities to user identities today is five to one (5:1) but according to Microsoft Security research, in the next 5 years that will be twenty to one (20:1). Therefore, bad actors are turning their attention to workload identities.
To help secure workloads, Microsoft will make Entra Workload Identities generally available in November 2022. At launch you will be able to take Workload Identities for a spin with a free 90 day trial. Pricing for Workload Identities is not yet available though.
The familiar security capabilities that have, until now, only been available for user identities will be expanded for workload identities, such as
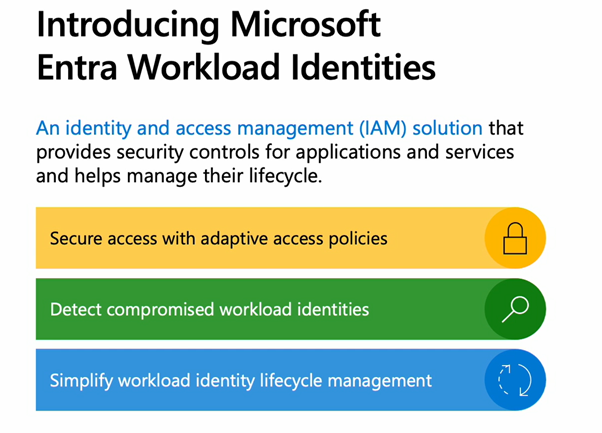
Figure 6 Security controls for workload identities (image source: microsoft.com)
Conditional Access for workload identities can leverage location-based policies for workload identities so that you can block access from outside trusted locations. Continuous Access Evaluation for workload identities protects Microsoft Graph targeted sign ins by instantly enforcing location-based controls.
When creating a new conditional access policy that you wish to target for workload identities, you need to specify what kind of identities the policy applies to by selecting “Workload Identities”:
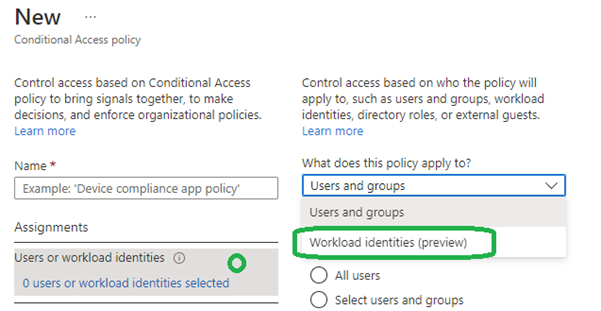
Figure 7 Select the type of identities in the assignments of Conditional Access policies (image source: microsoft.com)
Identity Protection (requires Azure AD Premium P2) can detect indicators of compromise, anomalous sign-ins or unauthorized changes to workload identities.
You can create a Conditional Access policy to block access when the AI determines the risk level of a service principal of Low, Medium or High.
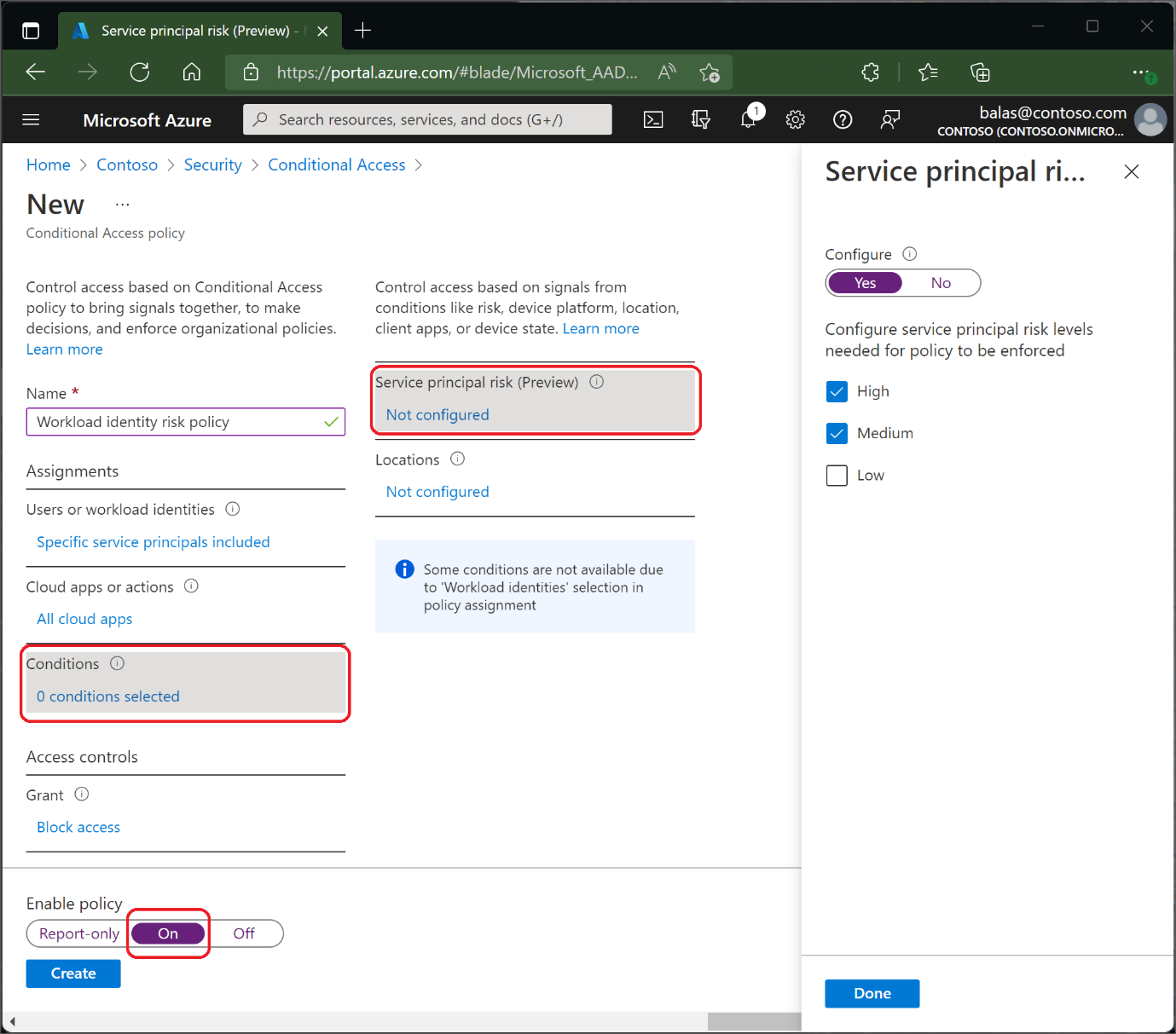
Figure 8 Risk-based conditions for service principals in Conditional Access (image source: microsoft.com)
You will now also see a few new tabs and blades in Identity Protection that pertain to workload identities. First, you will notice the new “Risky workload identities” blade where you can determine if the workload identity was compromised, then you can dismiss the account’s risk, or confirm the account as compromised.
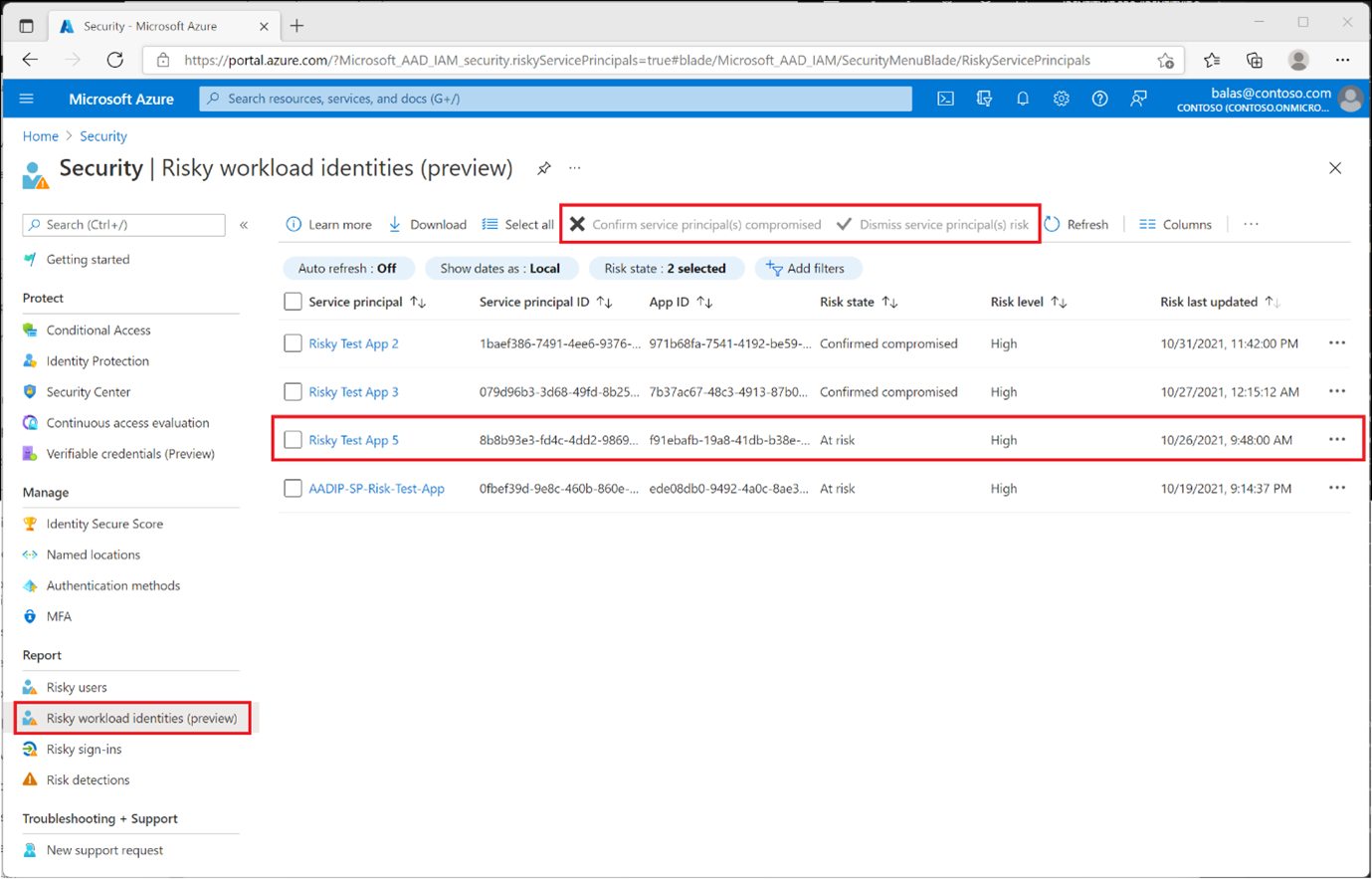
Figure 9 Risky workload identities blade (image source: microsoft.com)
The “Risk detections” blade also includes a “Workload identity detections” tab where you can identify workload identities that have been flagged for risk.
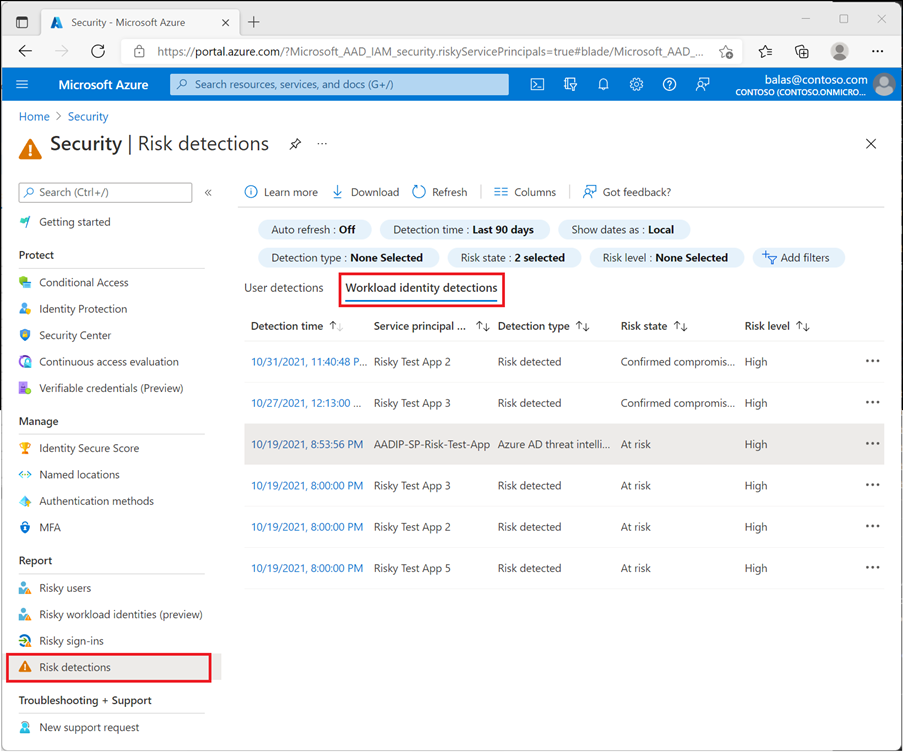
Figure 10 Workload identity detections tab in Risk detections (image source: microsoft.com)
Access Reviews will allow you to enforce least privileged access, delegate reviews, automatic revocation/extension with scheduled recurring review cadence on service principals in the scope section.
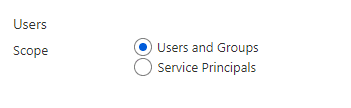
Figure 11 Users scope in Access Reviews (image source: microsoft.com)
In some regulated industries, user authentication requires the use of certificates or smart cards. In the past, you had to use on-premises Active Directory Federated Services (AD FS) together with a certificate authority.
AD FS has become a primary attack vector. Over the past year Microsoft have added more than 20 AD FS capabilities to Azure AD so that you can move off AD FS, Certificate Based Authentication (CBA) is one of the latest and removes the last major blocker for those regulated industry customers who want to move authentication to the cloud. Microsoft Entra Certificate Based Authentication is now Generally Available.
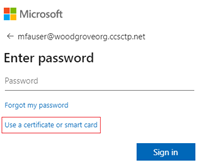
Figure 12 Sign in with certificate or smart card (image source: microsoft.com)
With Azure AD certificate-based authentication, customers can authenticate directly against Azure AD and eliminate the need for federated AD FS, which simplifies and reduces costs associated with your on-premises environment.
Azure AD CBA enables customers to adopt a phishing resistant authentication and authenticate with an X.509 certificate against their Public Key Infrastructure (PKI).
Phishing resistant authentication requires Password or biometric plus asymmetric key cryptographic processes such as Personal Identity Verification (PIV) cards, Common Access Cards (CAC) or FIDO2.
“This requirement for phishing-resistant methods is necessitated by the reality that enterprise users are among the most valuable targets for phishing. That problem can be mitigated by providing those users with phishing-resistant tokens, including the PIV cards that agency staff and partners are generally issued.”
M-22-09 Federal Zero Trust Strategy (whitehouse.gov)
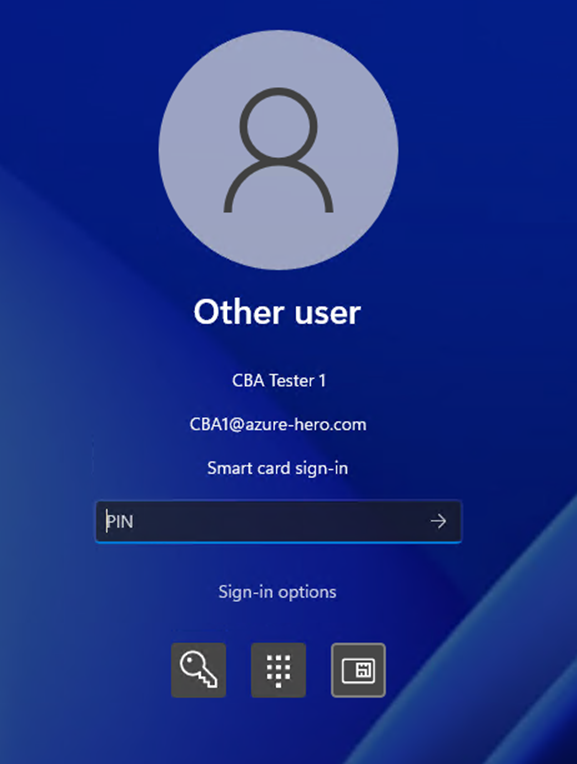
Figure 13 Smart card sign-in with CBA (image source: microsoft.com)
Users can authenticate using X.509 certificates on their smart cards directly against Azure AD at Windows sign-in. User presents the physical or virtual smart card to the Windows machine.
Virtual smart cards are functionally similar to physical smart cards. They appear as always-inserted smart cards. Because TPM-enabled hardware is readily available virtual smart cards can become a full replacement for other methods of strong authentication.
As with other AD FS authentication, you can pilot and control the usage of CBA using staged rollout. There is a new “Certificate-based authentication” toggle now in the portal.
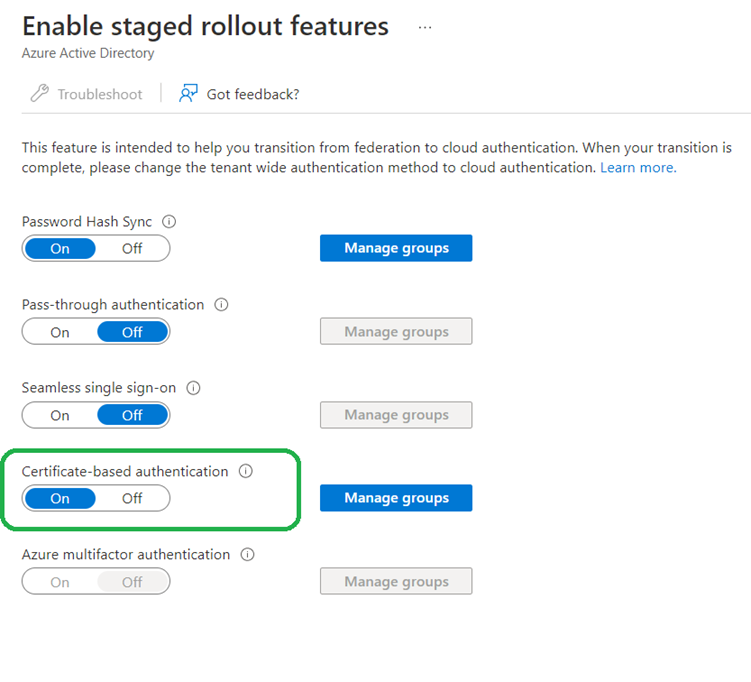
Figure 14 CBA staged rollout feature toggle (image source: microsoft.com)
Certificate-based authentication is a free feature. Every edition of Azure AD includes Azure AD CBA.
Now that Azure CBA is Generally Available as a phishing resistant authentication method, Conditional Access Authentication Strength is in Public Preview. With Authentication Strength, you’ll be able to require the use of phishing-resistant MFA. These new phishing-resistant MFA capabilities are critical for all customers, but especially those in regulated industries, such as United States federal agencies that must deploy phishing-resistant MFA to comply with the White House Executive Order on cybersecurity.
When accessing sensitive applications, admins can require phishing resistant MFA verification methods in a conditional access policy, such as:
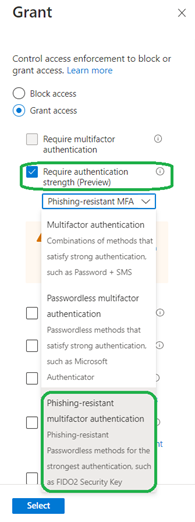
Figure 15 Conditional Access Grant Require authentication strength (image source: microsoft.com)
You can also create a custom authentication strength based on the authentication method combinations you want to allow.
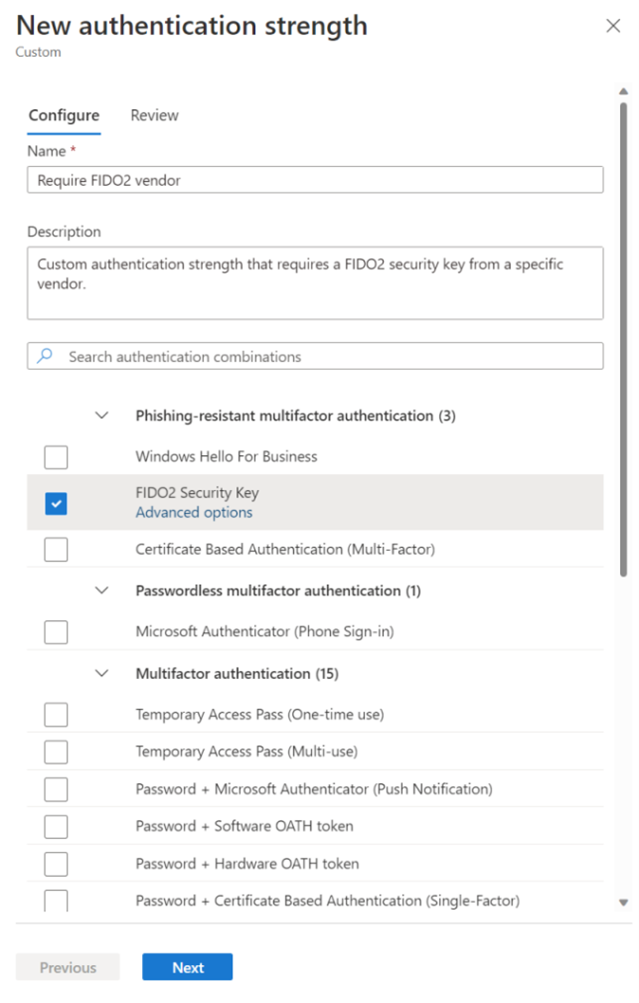
Figure 16 Custom authentication strengths (image source: microsoft.com)
To summarize, the new features and functionality to Microsoft Entra are:
Identity Governance – Enhancements made to Entitlement Management, Access Reviews and new Lifecycle Workflows. Additional Conditional Access capabilities related to Authentication Strengths and Certificate Based Authentication (CBA).
Workload Identities – Being able to protect, and manage previously unmanageable non-human accounts in Azure AD.
Figure 17 The full list of Entra features

For more information on Authentication Stengths, review Overview of Azure Active Directory authentication strength (preview) - Microsoft Entra | Microsoft Learn
For all the Microsoft Entra updates mentioned above, watch on demand, the Ignite Session “Secure access and improve efficiency with Microsoft Entra innovations that span Azure AD, Permissions Management, and more” from Joy Chik - President, Identity and Network Access at Microsoft.
Also take a look at the Ignite announcement blog: Do more with less—Discover the latest Microsoft Entra innovations - Microsoft Security Blog
Active Directory is the foundation of your network, and the structure that controls access to the most critical resources in your organization. The ENow Active Directory Monitoring and Reporting tool uncovers cracks in your Active Directory that can cause a security breach or poor end-user experience and enables you to quickly identify and remove users that have inappropriate access to privileged groups (Schema Admins, Domain Administrators). While ENow is not an auditing software, our reports reduce the amount of work required to cover HIPAA, SOX, and other compliance audits.
Access your FREE 14-day trial to accelerate your security awareness and simplify your compliance audits. Includes entire library of reports.

Microsoft Security MVP | Principal Architect @NBConsult | Speaker | Blogger. I am an Identity and Access Solutions Architect for NBConsult, a leading IT service provider in South Africa. I have 20+ years of experience in Microsoft enterprise technologies. I am passionate about Identity Governance and how it can help organizations achieve better security, compliance and productivity. I write blogs where I share my insights and tips on Application Governance.


The good people at ENow asked me to do a webinar on Identity and Authentication Management for...


Microsoft’s identity portfolio is huge and includes products and services like Active Directory, AD...