Deploying Outlook mobile securely in the enterprise (Part 2)

Dominik Hoefling MVP
Have you read Part 1 of this blog series yet? Enterprise Outlook mobile deployment is a hefty topic, which is why we had to break it up to two blogs. In Part 1, Dominik Hoefling goes over Outlook Mobile security basics, securing access to the service, securing the mobile client, and more!
Intune MDM and App Protection
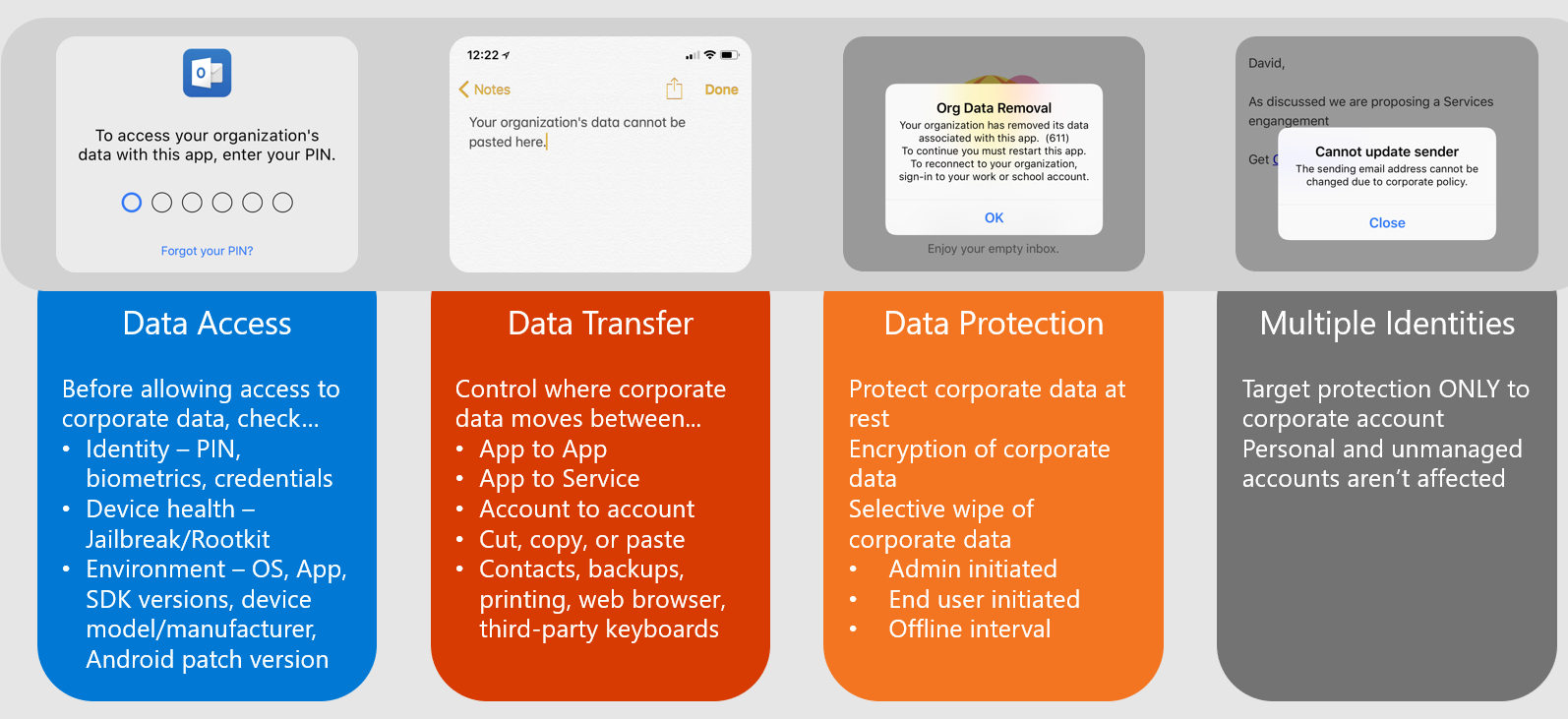
Intune App Protection Policies (APP) deploys a policy to an app that protects the corporate data within that app without requiring you to enroll the device.
All Office apps are built with the multiple identity construct in mind. This means it takes care of consumer accounts as well as commercial accounts like Outlook, where you can have a work email account and personal email account. We can imply and target protections to the corporate identity because everything is grounded to the identity in EM+S. We can protect only the corporate data and leave the personal data alone. It’s possible to target only the corporate data and encrypt it – and not only encrypt it, also wipe the corporate data if needed.
The data access protection mechanism ensures that apps are only accessible with protection capabilities, like a PIN, or biometric gesture and ensures the compliance of the corporate data. Additionally, we can determine through the Intune SDK whether the device is jailbroken or rooted and block access or wipe the device. Also device variables can be queried like minimum operation system version, app version, SDK version, etc.
Data leak with an unprotected personal device can be prevented by data transfer mechanism. This means we can configure how data is allowed or not allowed to be transferred between the work account and personal account. As well you can decide if data between different apps is allowed to be transferred or not.

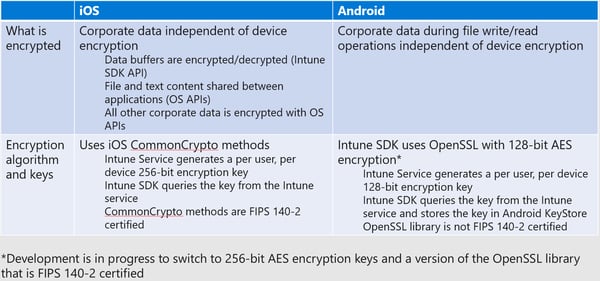
Application Configuration PoliciesFrom an encryption perspective, you may be thinking if I don’t enroll the device, how do I ensure that encryption is enabled on that device? The answer is, we don’t care if the encryption is enabled on the device, because we will encrypt the contents of the corporate data independently of the device encryption status.
Use app configuration policies in Intune to provide configuration settings for an iOS or Android app. These configuration settings allow an app to be customized. You do not assign these configuration policies directly to users or devices. Instead, you associate a configuration policy with an app, and then assign the app. The configuration policy settings are used when the app checks for them, typically the first time it is run. You can assign an app configuration policy to a group of users and devices by using a combination of include and exclude assignments.
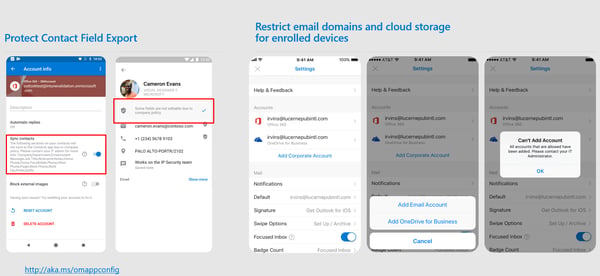
Securing the data in Office 365
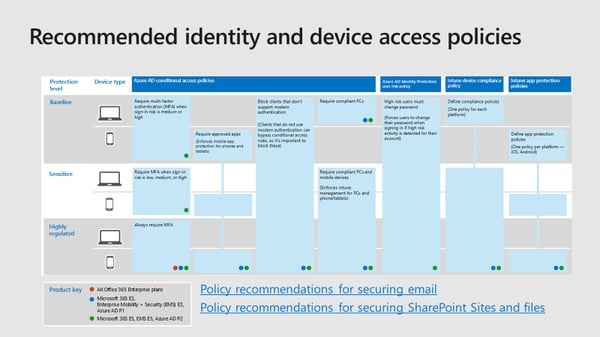
The following screenshot provides recommended identity and device access polices for your Outlook mobile deployment in the enterprise.
Roadmap for Outlook Mobile
There is a huge roadmap for features that will be available for Outlook mobile for both iOS and Android devices in the future. Some great features that will be released in 2019 are:
- Secure Multipurpose Internet Mail extensions (S/MIME): June CY2019
- Support shared mailboxes: June CY2019
- Favorite notifications: May CY2019
- Native labeling sensitive messages: Q4 CY2019
- Create Group calendar events: Q4 2019
More features for Outlook mobile which are recently launched or in development can be found here.
End-User Experience Monitoring
In a cloud-based world, admins are often left in the dark, ENow turns the lights back on! ENow's synthetic transactions test common Office 365 applications (OneDrive, Teams, SharePoint) allowing admins to proactively test and easily verify their end users' experience. 

Dominik Hoefling MVP
Dominik is a Microsoft MVP primarily specializing in Microsoft Exchange, Exchange Online and Office 365. Dominik currently works for a German consulting company, AtWork. At atwork, Dominik focuses on designing and building message infrastructures and cloud technologies. Dominik has worked in IT since 2004, primarily with Exchange Server but also has experience with Windows Server, Active Directory, Azure, Office 365, Unified Messaging and various third party products.
Related Posts

Mobile Device Management (MDM) In Office 365

Dominik Hoefling MVP
The growth of mobile devices, such as smartphones and tablets, changed the world rapidly. Today,...
