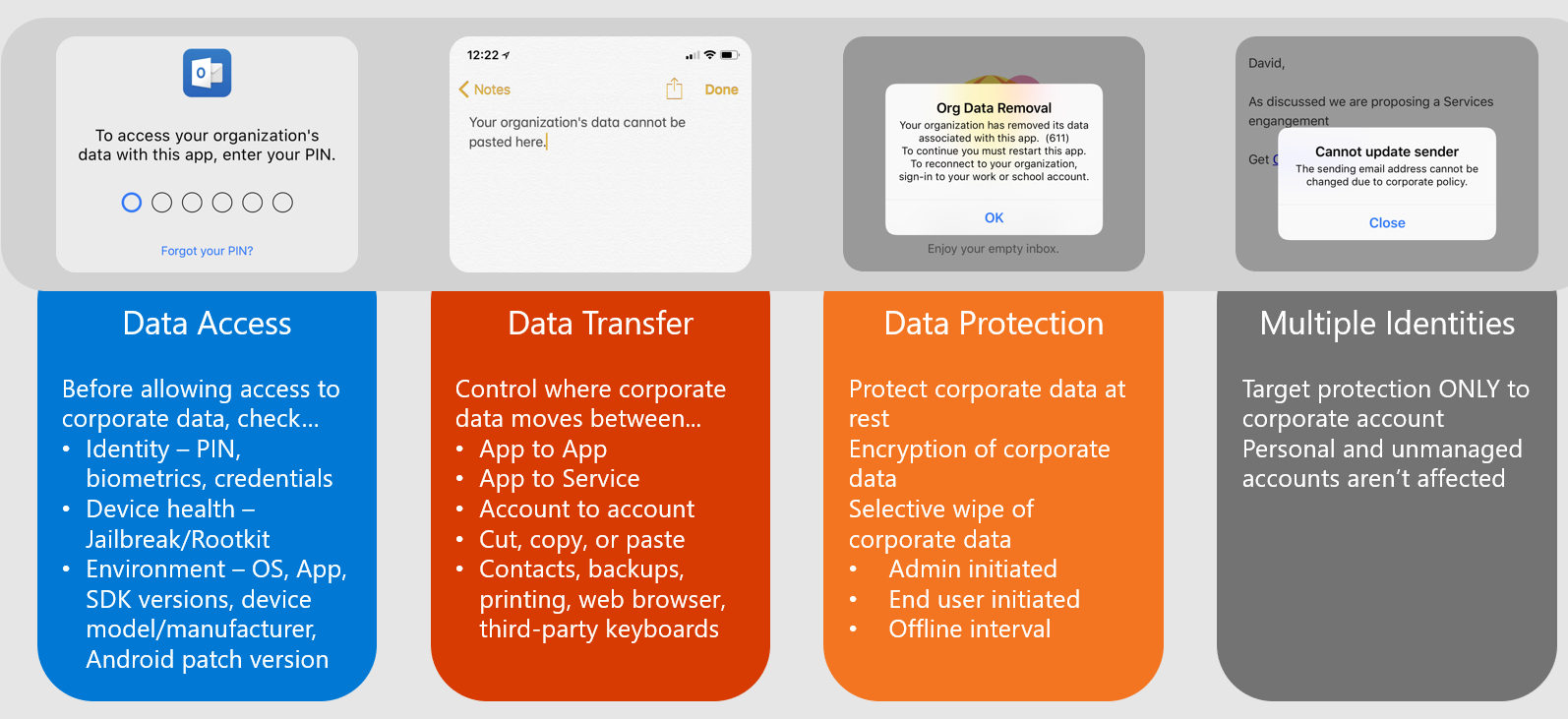
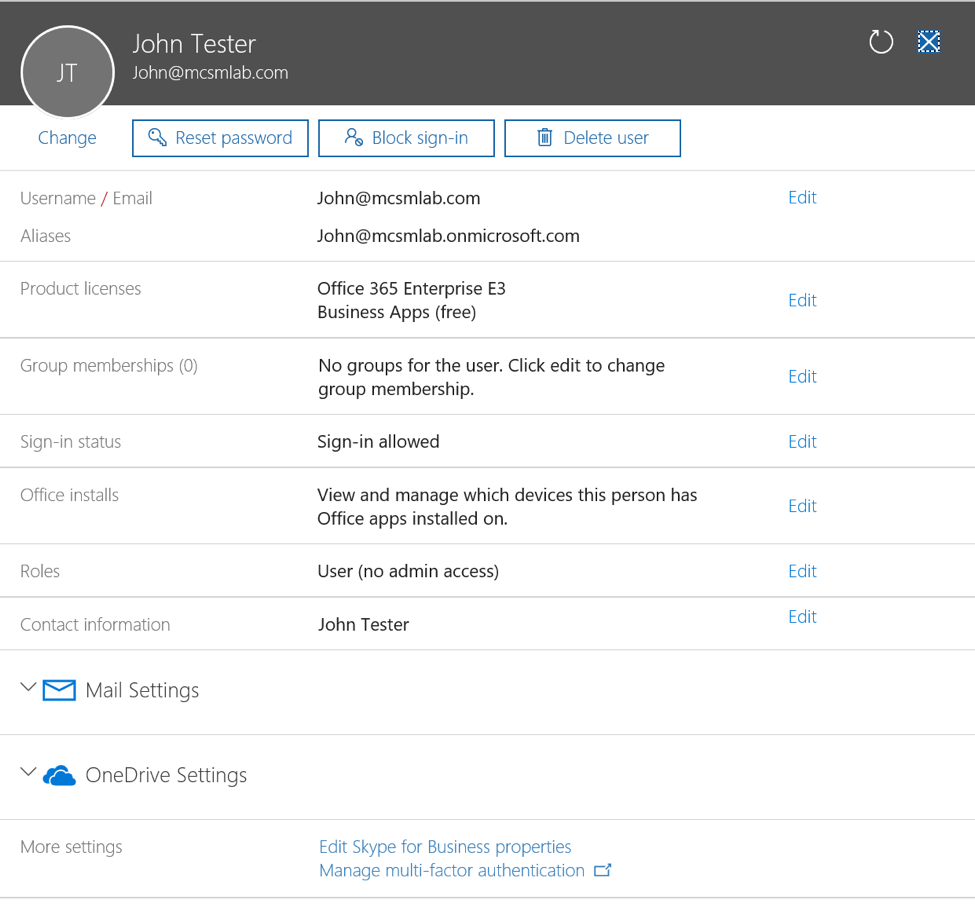
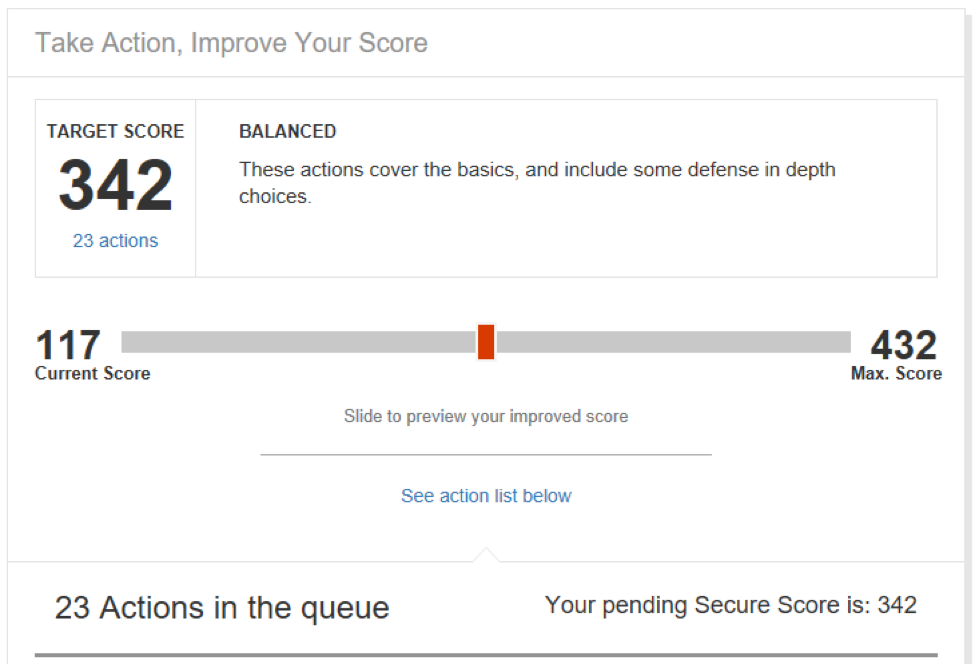
Office 365 Security: Do You Have a People Problem?
Many organizations regard their people as their greatest asset. There is no disputing that the ability to hire great talent is a critical component to success, but in today’s pandemic-work-from-home world these great assets could also pose the greatest risk to your business.