Administrative Units Management in Azure Active Directory
Administrative Units Management in Azure Active Directory
Since writing this blog post in May 2018...

Office 365 comes with a set of admin roles that can be assigned to users within your organization. Each admin role maps to common business functions and gives your users permissions to do specific tasks in the Office 365 admin center and Windows PowerShell.
This is especially true for large organizations or universities with multiple brands or decentralized administration within a single Office 365 tenant, the default admin roles can cause headaches. While the delegation of permissions in Exchange Online works very well with Role Based Access Control (RBAC), other applications and services are hard to manage at a granular level. For example, license management or helpdesk for different countries, brands, and organizations. In these organizations, only a subset of administrative users are allowed to edit properties based on their region or brand.
Azure Active Directory administrative units are a container of resources that can be used for delegating administrative permissions and applying policies to a subset of users. They enable central administrators to delegate permissions based on region, brand or to set a policy at a granular level. It simply groups your users into logical units. An admin will be able to perform various tasks against all users within the scope of an administrative unit.
At the time of writing, administrative units are still in public preview and the global admin needs to have an Azure Active Directory Premium licensed assigned while users within the administrative units needs Azure Active Directory Basic licenses. In this preview, only users can be assigned to resources. Once created and populated, the administrative unit can be used as a scope to restrict the granted permission only over resources contained in the administrative unit. Also, there are only two roles available: User Account Administrator and Helpdesk Administrator.
Before we can start, the Azure Active Directory Module public preview release needs to be installed:
Install-Module AzureADPreview
Connect to Azure Active Directory with the Office 365 global admin:
Connect-AzureAD
This blog post covers three examples of delegated administration for the role “User Account Administrator” for a specific region, “Helpdesk Administrator” for users within a specific department, and we will scope an Exchange administrator to a specific administrative unit.
The following admin user accounts are available:
Get-AzureADUser
ObjectId DisplayName UserPrincipalName UserType
-------- ----------- ----------------- --------
f1851b74-617d-40c9-8943-30ac58e84f48 Dominik Hoefling (atwork) info@dominikhoefling.com Member
6d381b8c-7e16-4601-81ab-79333efb61c6 Dominik Hoefling (Exchange Lab) info@exchange-lab.de Member
“Dominik Hoefling (Exchange Lab)” is the user account administrator for US, Dominik Hoefling (atwork)” is the helpdesk administrator for Germany, and as well the Exchange administrator for a certain administrative unit.
Note: There are currently no parameters like -Department, -Office, or -Country. And there is no dynamic membership, you must manually add the users to the administrative unit, which also means you must keep it up to date. The -Country attribute in this blog is only used to easily add members to different administrative units.
User Administrator
The requirement is to have multiple user account administrators only for a subset of users within a specific region. This example allows the privileged user “Dominik Hoefling (atwork)” to administrate users based in US and deny administration for users located in Germany.
Run steps 1 – 5 with a global admin account:
DisplayName: Dominik Hoefling (Exchange Lab)
ObjectId: 6d381b8c-7e16-4601-81ab-79333efb61c6
UserPrincipalName: info@exchange-lab.de }
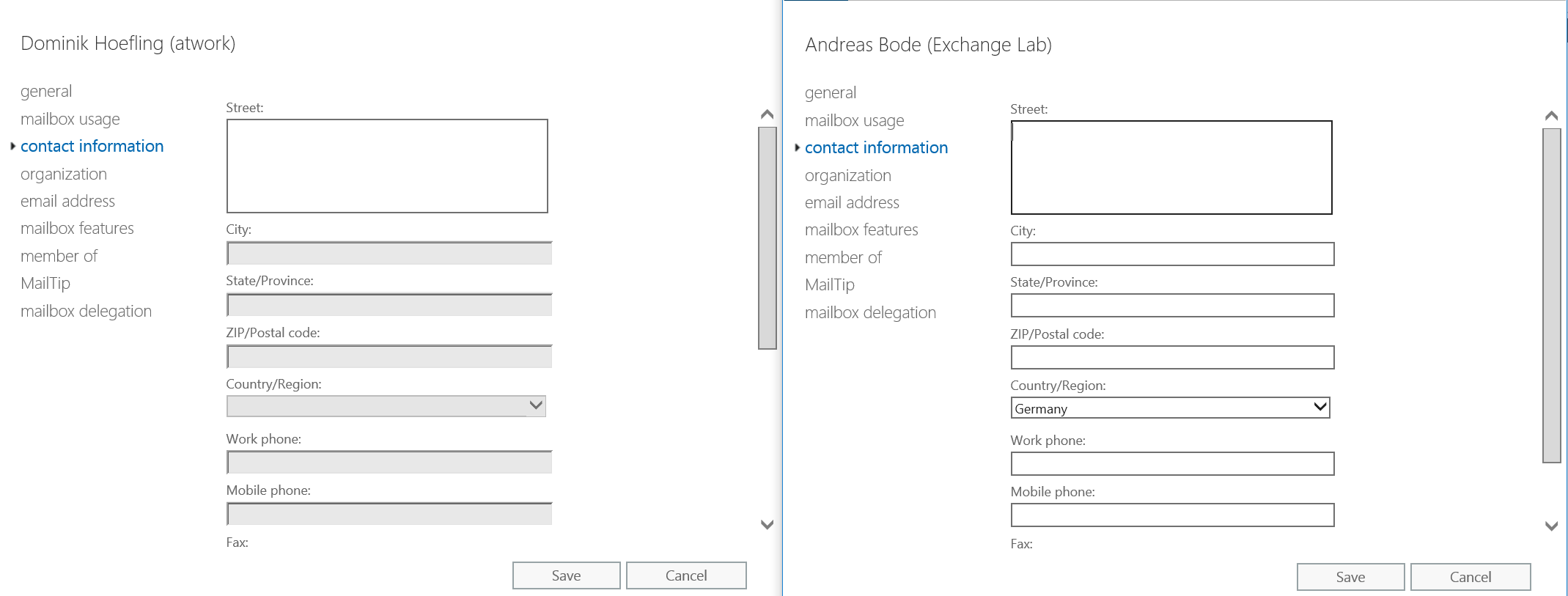
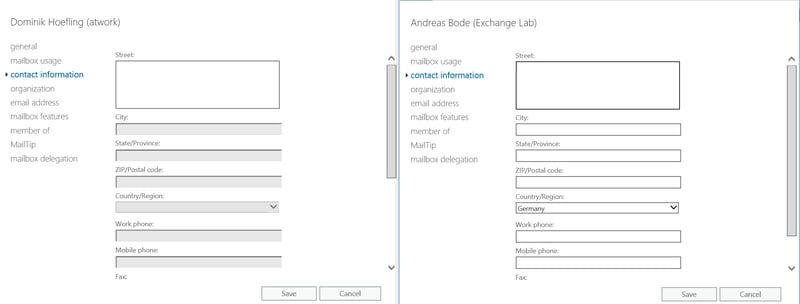
Only members in the administrative unit (step 3) can be viewed and edited with the “User Account Administrator” privileges.
The same behavior applies to Windows PowerShell:
Set-AzureADUserPassword -ObjectId "f1851b74-617d-40c9-8943-30ac58e84f48" -Password $password
Set-AzureADUserPassword : Error occurred while executing SetUser
Code: Authorization_RequestDenied
Message: Insufficient privileges to complete the operation.
HttpStatusCode: Forbidden
HttpStatusDescription: Forbidden
HttpResponseStatus: Completed
At line:1 char:1
+ Set-AzureADUserPassword -ObjectId "f1851b74-617d-40c9-8943-30ac58e84f ...
+ ~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
+ CategoryInfo : NotSpecified: (:) [Set-AzureADUserPassword], ApiException
+ FullyQualifiedErrorId : Microsoft.Open.AzureAD16.Client.ApiException,Microsoft.Open.AzureAD16.Graph.PowerShell.Custom.C
mdlet.SetUserPassword
Helpdesk Administrator
The requirement is to have multiple helpdesk administrators for only a subset of users within a specific region. You can go through the same steps to configure the “User Account Administrator” administrative unit. If required, change the variables or the user filter on a different region, country or any other attribute. You only have to take care of the correct ObjectId’s of the administrative unit, admin role and your users.
To begin with, it is not possible to create other administrative unit admin roles at the time of writing. For example, if you want to add the scoped role membership to the “Exchange Service Administrator”, you will receive the following error message:
Hopefully Microsoft will add more granular privileged admin roes in the future.
Connect to ExHowever, you can scope Exchange Online Role Based Access Control (RBAC) management roles to an administrative unit. In this example, we are using the built-in “Mail Recipients” role and delegating the admin role to the “Dominik Hoefling (Exchange Lab)” admin who can administrate only US-users within the formerly created administrative unit.
Azure Active Directory administrative units are a good step forward, but they definitely need some more granular privileged admin roles that can be used with other Office 365 applications and workloads (i.e. license management based on different companies and/or countries. As for now, you can scope the built-in roles “User Account Administration” and “Helpdesk Administrator”). For Exchange Online, you can scope RBAC to administrative units as well, which means you can cover mostly every requirement and workload at least for Exchange.



Using Microsoft Graph PowerShell SDK
In my previous article about creating custom roles for...