AAD custom roles for EXO administrators
Using Microsoft Graph PowerShell SDK
In my previous article about creating custom roles for...

Part #1: Introduction Microsoft Graph PowerShell SDK
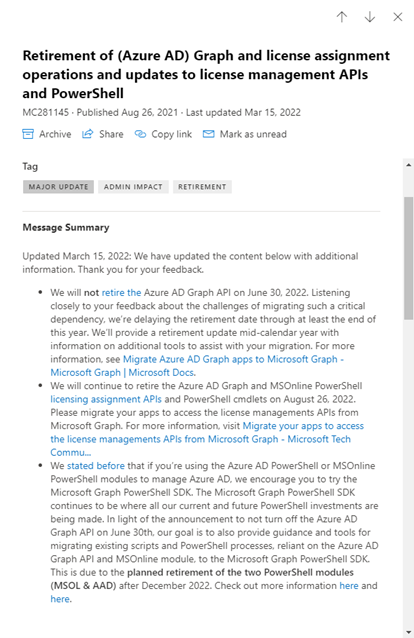
As mentioned in a previous article about Azure AD custom roles for Exchange Online administrators here, Microsoft has planned retirement of their PowerShell modules. You can read more about this in your Message Center in MC281145:
What does it mean?
Microsoft is putting all its investments and efforts in Microsoft Graph PowerShell SDK. To be more precise into Microsoft Graph itself. The PowerShell SDK derives from all the features and capabilities of Microsoft Graph and not vice versa.
With this, the existing PowerShell modules might still work. However, if you encounter issues managing your objects or new features light up in Microsoft Graph, you’re most likely left alone.
As the current deadline is set to December 2022, it’s time to start getting familiar with Microsoft Graph PowerShell SDK. You can split this in 3 parts:
Azure AD Graph API
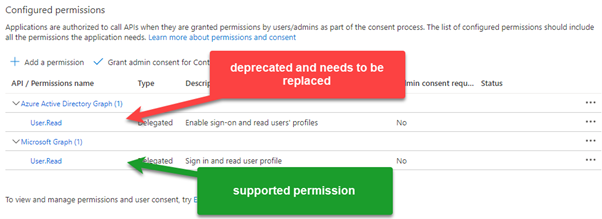
This is now part of legacy APIs. When you have applications in your tenant registered long time ago, you have used these permissions. Microsoft makes it hard for you to add them to an application:
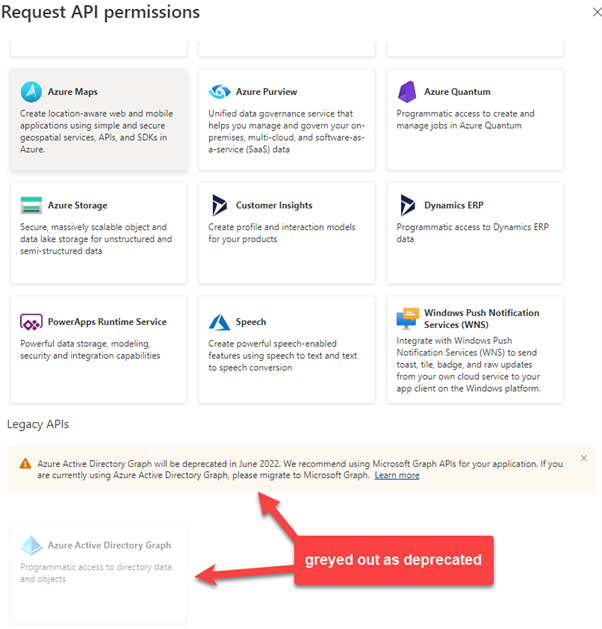
But you would still be able to add by searching for the AppID on the tab APIs my organization uses.
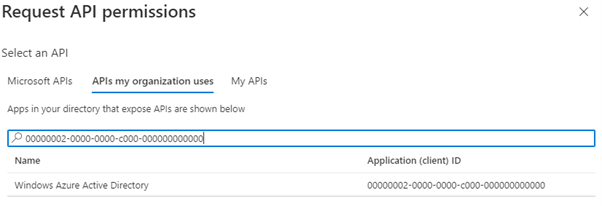
Note: You should not add these permission to existing applications!
The reason why you see here the example, I want to highlight the AppID. With the AppID you can search in your tenant for applications configured with these deprecated permissions.
Note: As this is a complex query you need to use ConsistencyLevel and CountVariable. Read more about this here. Once you identified them, you can replace the existing permissions with the once from Microsoft Graph.
Example:
$appParams = @{
Filter = "requiredResourceAccess/any(r:r/resourceAppId eq '00000002-0000-0000-c000-000000000000')"
ConsistencyLevel = "eventual"
CountVariable = "CountVar"
All = $true
}
Get-MgApplication @appParams
Note: As this is a complex query you need to use ConsistencyLevel and CountVariable. Read more about this here.
Once you identified them, you can replace the existing permissions with the once from Microsoft Graph.
Example:
Daily work
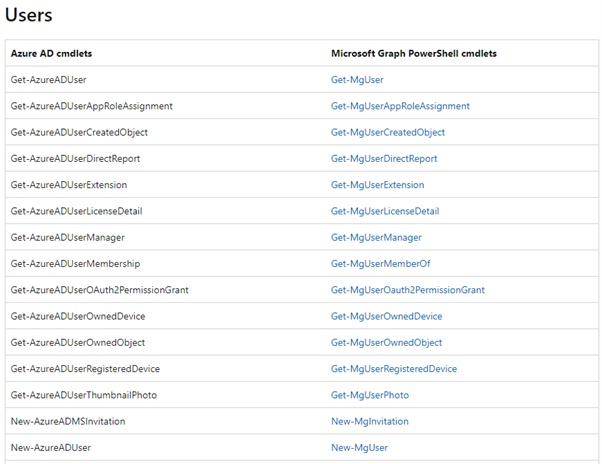
Of course, this has a major impact on you as you need to switch from a well-known PowerShell module to a new one. Besides the installation you need to get familiar with the new cmdlets. A good starting point can be found here as it helps you to find the corresponding cmdlet.
Example:
Instead of Get-AzureADUser you would run Get-MgUser:
Another really good resource is coming from community:
You can install the add-on for either Chrome or Edge and while you are working in the Azure AD portal, you can see the corresponding Microsoft Graph and PowerShell SDK requests or commands.
Also, a great community driven source can be found on GitHub:
You can find a lot of examples (simple and complex), which might be useful for your daily tasks.
Scripts (e.g.: used for automation)
This is the most crucial part in your transition. There is no way to screen all your developed scripts in an automated way. You need to check every script carefully. This includes not only to replace old with new cmdlet. You also need to check returned types for values. What was before a GUID it can be now a string!
Conclusion
As you might realize, this is not an easy task. However, Microsoft builds a foundation for the future. No one wants another PowerShell module. We must deal already with too many modules even from the same product group (e.g.: AzureAD and AzureADPreview ). Having all of them combined into one is highly appreciated.
Support for authentication without a user, automation is made much simpler than it was before. We also can expect high performance, more reliable sessions, including the ability to access data across multiple workloads!
Active Directory is the foundation of your network, and the structure that controls access to the most critical resources in your organization. The ENow Active Directory Monitoring and Reporting tool uncovers cracks in your Active Directory that can cause a security breach or poor end-user experience and enables you to quickly identify and remove users that have inappropriate access to privileged groups (Schema Admins, Domain Administrators). While ENow is not an auditing software, our reports reduce the amount of work required to cover HIPAA, SOX, and other compliance audits.
Access your FREE 14-day trial to accelerate your security awareness and simplify your compliance audits. Includes entire library of reports.


Using Microsoft Graph PowerShell SDK
In my previous article about creating custom roles for...
.png?height=175&name=Untitled%20design%20(4).png)

In one of my other articles “Accessing Exchange Online Objects” I...