Office 365 Basic Authentication Update
Almost a year ago, in March 2020, I wrote an article called Microsoft stops basic authentication,...


The last couple of years we have seen several security breaches in IT, leading to serious impact and financial losses. Not only in the United States, but also in the rest of the world. Last year here in Holland we have seen two respected companies in a lawsuit, where one company was compromised, leading to a financial loss of a 7-digit number of the other company. The first company was running their environment in Office 365, but because of a weak password, the mailbox of a financial controller was compromised.
It could easily have been prevented by using Multi-Factor Authentication (MFA). In my own customer base there are also examples of security breaches, including CFO fraud which resulted in a financial loss which also could have been prevented easily.
MFA comes with modern authentication in Office 365. Modern authentication is based on tokens and is much safer than the traditional basic authentication which is based on username and password. Username and password are sent across the wire with every request, and it is sent in clear text so easy to capture. Microsoft started the deprecation of basic authentication in 2019. Because of the Covid-19 pandemic it was slowed down a bit but it is still progressing. And basic authentication will be turned off in the (near) future, there’s no doubt about that. I have written about the deprecation of basic authentication before on this site:
If you haven’t started moving to modern authentication, I strongly recommend reading these articles as they explain the difference between basic authentication and modern authentication and the steps you must take to move to modern authentication.
All services in Office 365 supports modern authentication. There are still scenarios though where you can run into issues when moving to modern authentication. For example, I have been working on a situation where a 3rd party vendor moved his application to Microsoft Azure and as such was able to use modern authentication. However, the customer was running an Exchange hybrid organization, and this specific application was not able to successfully logon to the mailboxes that were still on Exchange 2016 on-premises. Vice versa is more common, where an application needs to remain on-premises because it cannot work with modern authentication in Exchange Online. In both scenarios it was not the customer’s problem, but the 3rd party vendor had to work on a solution.
Another issue you must be aware of is mobile devices. Apple’s iOS support OAuth (=modern authentication) since iOS11 so for new accounts this should not be a problem. However, if you configured the native mailapp in an older version and migrated to the latest version of iOS, the old configuration is kept. So, you will end up with a new iPhone that supports OAuth but under the hood still uses basic authentication.
I haven’t been testing Android devices lately, there are so many versions available, so it is difficult to make general comments. You must monitor logins in Azure AD to see if devices are still using basic authentication.
POP3 and IMAP4 in Office 365 support modern authentication. One question that pops-up on a regular basis is if Microsoft will support modern authentication for POP3 and IMAP4 within Outlook. That will not happen. When using Outlook, you must use Mapi/Http to connect to Exchange Online. If for some reason you must use POP3 or IMAP4 you must use a client like Thunderbird (which supports OAuth).
Microsoft is actively monitoring basic authentication usage and if you are not using basic authentication in your tenant, Microsoft will turn it off in your tenant. Basic authentication can be turned off completely, but also on a per protocol basis. Remember that you can always turn it back on manually.
When Microsoft is planning to turn off basic authentication in your tenant, you will receive an announcement first as shown in the following screenshot:
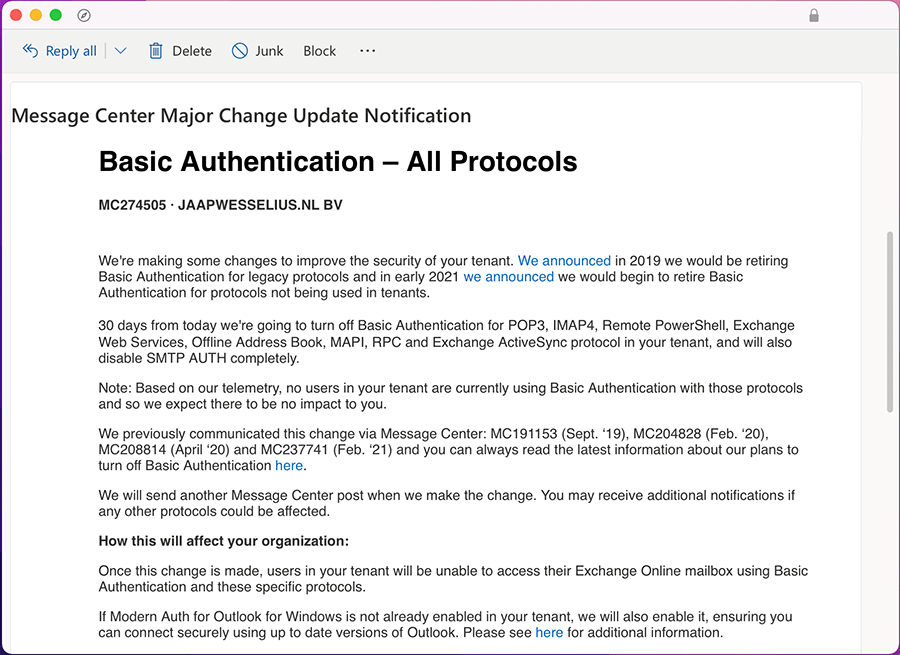
The good news is that you can opt out at this moment. The bad news is that Microsoft will turn off basic authentication completely by the end of 2022. So, if you don’t act now you might be surprised later this year. Yes, this will hurt customers and it will hurt Microsoft and there will be serious noise when it is turned off, but it is for the better.
If you have some spare time (approx. 45 minutes) I can recommend listening to this podcast where Microsoft Program Manager Greg Taylor talks about email, security and the decommissioning of basic authentication. It’s an interesting talk: https://runasradio.com/Shows/Show/806
On-premises components, such as AD FS, PTA, and Exchange Hybrid are critical for Office 365 end user experience. In addition, something as trivial as expiring Exchange or AD FS certificates can certainly lead to unexpected outages. By proactively monitoring hybrid components, ENow gives you early warnings where hybrid components are reaching a critical state, or even for an upcoming expiring certificate. Knowing immediately when a problem happens, where the fault lies, and why the issue has occurred, ensures that any outages are detected and solved as quickly as possible.
Access your free 14-day trial of ENow’s Exchange Hybrid and Office 365 Monitoring and Reporting today!

Jaap is a Microsoft MVP for Office Apps and Services. Jaap is an independent consultant, primarily focusing on Exchange server, Skype for Business and Office 365.


Almost a year ago, in March 2020, I wrote an article called Microsoft stops basic authentication,...


Welcome to part 3 of "Addressing the Office 365 Monitoring Gaps". In part 1, we discussed the...