How Microsoft Improved Its Identity Products and Services - September 2022
Microsoft’s identity portfolio consists of many products, like Active Directory, AD FS, Azure AD...


Christmas is arguably one of the few time periods every year, where droves of IT people are off work, globally. This makes December an odd month from an IT Pro point of view. Especially, since it seems to be high season for adversaries. With your Microsoft-oriented networking infrastructure up to date and monitoring in place, however, there is little to worry about.
If you were among the ‘lucky’ people to run shifts this holiday season, this blogpost might not contain anything new. If you just got out of ‘hibernation’, Enow Software is here to get you back up to speed.
After its November 2022 updates, some argued Microsoft had work to do. Admins who were experiencing challenges with these updates created registry keys on their domain controllers, changed group policies and/or installed the out-of-band updates manually to avoid and/or remediate:
For those who awaited and held off on installing the November 2022 updates, the December 2022 cumulative updates are good news. These updates offer solutions for all the Active Directory issues that arose previously. No new Identity-related issues were reported, either. Updating Domain Controllers required some timing though, as December 2022’s second Tuesday was the latest possible Tuesday possible: December 13th. This left admins with a mere eight working days to get updating sorted out before Christmas.
After applying updates to Azure AD Connect, Apple-, Android-, Intel-, Citrix-, ZyXEL, Fortigate-, Netgear- and VMware-based assets, admins could enjoy the holidays knowing that they at least applied the latest updates. From Microsoft’s 2022 Digital Defense Report, we learned that this basic security hygiene measure helps protect against 98% of attacks:
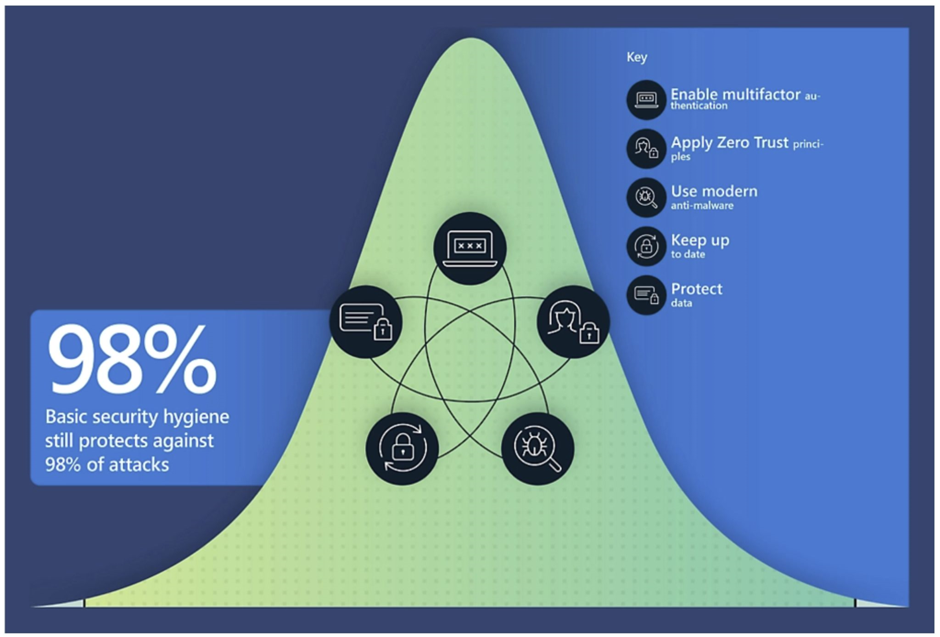
Another big pillar under that percentage is having people in the organization register multi-factor authentication.
Last month, we discussed how Microsoft Authenticator app v6.6.8 and beyond are now FIPS-140 compliant. This month, the good news on the Authenticator App is the general availability of multiple Password-less Phone Sign-in for iOS Devices. In preview, this feature was already heavily embraced by consultants, students, and others with multiple accounts in Azure AD. Now, the feature can be used, even without permitting Microsoft access to telemetry data.
The bad news, however, is that Microsoft is actively communicating the pending demise of Authenticator app support for Apple watches. It simply isn’t compatible with the Number Matching feature that Microsoft will be pushing from the end of February 2023 (planned).
Simply registering any multi-factor authentication method won’t cut it, though. It’s important that people register secure multi-factor authentication and password-less sign-in methods with secure settings.
One goal that Microsoft actively works towards is a converged authentication methods policy. This feature became public preview in December and promises one blade to manage available authentication methods to people in the organization. Today, settings that apply are scattered throughout the legacy PhoneFactor portal, the self-service password reset settings, on the Authentication Methods blade in the Azure AD portal and in the Entra portal. Expect to be able to migrate settings from those first two locations to the latter. Combined with Authentication Strength, this provides control on what methods people can register and use from one location. Additionally, expect to be able to manage the policy through Microsoft Graph and PowerShell.
Managing Azure AD from the command-line got a major boost anyway in December 2022, albeit in Public Preview again. Aligning to Microsoft Ignite 2022’s motto of ‘do more with less’, Microsoft Graph PowerShell SDK v2 offers more functionality while requiring less disk space and less time. Admins who like to authenticate using managed identities, client secret credentials, certificates and/or environment variables can now do so.
In its effort to help organizations onboard to Azure AD as their highly available and highly secure identity platform for apps, Microsoft made its on-premises application provisioning functionality generally available. This means that Azure AD can now be used to provision and deprovision user objects in on-premises apps, when they support SCIM, or use an LDAP- or SQL Server-based backend. Of course, this functionality is not needed when the app uses Active Directory. Other apps can now be integrated to Azure AD using the Azure AD Connect Provisioning Agent.
Speaking of the Azure AD Connect Provisioning Agent… This piece of software underpins the forementioned app provisioning features, but also supports the HR sync process from SuccesFactors and WorkDay to Active Directory and Azure AD Connect Cloud Sync.
Microsoft announced that Azure AD Connect Cloud Sync (and not Azure AD Connect) will be the tool where Microsoft continues to invest in. Organizations are asked to consider using Cloud sync first, as it offers resiliency, only a small on-premises footprint and thus lower costs. Today, Cloud Sync isn’t quite on-par with Azure AD Connect, but Microsoft aims to close the gap.
Perhaps a good approach is to compare the features every time you manually update Azure AD Connect to a newer version. After switching to Cloud Sync, these manual updates will be a thing of the past.
Defender for Identity v2.195, released on December 7th, 2022, includes improvements and bug fixes for the internal sensor infrastructure. It is now also available in the Australia East region. For organizations in the Sydney region, this means that their new Defender for Identity implementation will be hosted closer to ‘the Harbour City’ than ever before.
A slow December month equals ample opportunity to get the Identity real estate of the organization in tip-top shape. In December 2022, Microsoft offered quite some pointers to keep going well into 2023 with optimizing Active Directory and Azure AD to address the needs of the organization. If you haven’t started yet, this is a perfect moment to get started!
Active Directory is the foundation of your network, and the structure that controls access to the most critical resources in your organization. The ENow Active Directory Monitoring and Reporting tool uncovers cracks in your Active Directory that can cause a security breach or poor end-user experience and enables you to quickly identify and remove users that have inappropriate access to privileged groups (Schema Admins, Domain Administrators). While ENow is not an auditing software, our reports reduce the amount of work required to cover HIPAA, SOX, and other compliance audits.
Access your FREE 14-day trial to accelerate your security awareness and simplify your compliance audits. Includes entire library of reports.

Sander's qualities extend beyond the typical triple-A stories in the area of Identity and Access Management. Of course, authentication, authorization and auditing are necessities but my out of the box solutions get the most out of software, hardware and the cloud. Rapid technological advancements have resulted in cutting-edge solutions around Active Directory, Azure Active Directory and Identity Management. Keeping up with these is just a small challenge, compared to my true goal: helping people use the technology on a daily basis. In a way that ICT is not a mere hurdle, but an infinite enabler. His work as a consultant, blogger and trainer are all means to achieve this goal. His multiple Microsoft Most Valuable Professional (MVP) status, Veeam Vanguard status and extensive certification aids him. Through direct communications with the product teams in Redmond, he remains up to date, exchanges feedback and accelerates support. Sander is also a Virtual Product Owner for AppGov and ENow.


Microsoft’s identity portfolio consists of many products, like Active Directory, AD FS, Azure AD...


Microsoft’s identity portfolio is huge and includes products and services like Active Directory, AD...