Active Directory Monitoring: Backup and Recovery - Options for AD DS
In Part 2 of this series, we'll discuss backup and recovery options for Active Directory Domain...

This is a 5-part series discussing how to backup and restore objects for Active Directory modules in Windows Server which is a critical component of Active Directory Monitoring for any organization.
Active Directory Domain Services (AD DS) does not always require a restore from a full backup. When objects are deleted in AD DS, they are moved to what is called the “Deleted Objects” container. When an object is moved to this container it will be stripped of important attributes. You will never be able to retain linked attribute values (ie: group membership).
In order to use this functionality you will need to determine if the Active Directory Recycle Bin feature has been enabled in you AD DS enterprise. Let’s say, for example, that the AD Recycle Bin feature has not been enabled. This means that a deleted object will remain in the system as long as it has not been scavenged by the garbage collection process (the cleanup process that will remove stale records) after reaching its tombstone lifetime (180 days). Consequently, you would be able to reanimate this deleted object.
You should note that AD DS runs garbage collection every 12 hours by default and does two things:
To reanimate a deleted object, you will need to use the LDP tool (ldp.exe). This is a command line utility where you can run Lightweight Directory Access Protocol (LDAP) searches against your AD implementation. The steps for reanimating a deleted object are listed below:
|
1. |
Click Start, and in the Start Search box, type Ldp.exe. Press Ctrl+Shift+Enter, which executes the command as an administrator. |
|
2. |
In theUser Account Control dialog box, click Use another account. |
|
3. |
In the Username box, type the username of an administrator. |
|
4. |
In the Password box, type the password for the administrative account, and then press Enter. |
|
5. |
Ldp opens. |
|
6. |
Click the Connection menu, click Connect, and then click OK. |
|
7. |
Click the Connection menu, click Bind, and then click OK. |
|
8. |
Click the Options menu, and then click Controls. |
|
9. |
In the Load Predefined list, click Return Deleted Objects, and then click OK. |
|
10. |
Click the View menu, click Tree, and then click OK. |
|
11. |
Expand the domain, and then double-click CN=Deleted Objects,DC=adatum,DC=com. |
|
12. |
Right-click the deleted object, and then click Modify. |
|
13. |
In the Attribute box, type isDeleted. |
|
14. |
In the Operation section, click Delete, and then press Enter. |
|
15. |
In the Attribute box, type distinguishedName. |
|
16. |
In the Values box, type the distinguished name of the object in the parent container or the organizational unit (OU) into which you want the object’s restoration to occur. |
|
17. |
In the Operation section, click Replace, and then press Enter. |
|
18. |
Select the Extended check box. |
|
19. |
Click Run, click Close, and then close LDP. |
|
20. |
Use Active Directory Users and Computers to repopulate the object’s attributes, reset the password for a user object, and enable the object, if disabled. |
The Recycle Bin feature of Active Directory came about in Windows Server 2008 R2. In order to be able to use this tool, the domain and forest functional levels must be at Windows Server 2008 R2 or newer. The benefit of using the Recycle Bin is that it will preserve all link-valued and non-link-valued attributes after it has been deleted. This means all objects will restore exactly the way they were when they were deleted. Since the object can be fully restored with all attributes, the object is referred to as “logically deleted”. So, in the case of a user object that was deleted, this mean the object can be restored with all group memberships and access rights intact. Active Directory Recycle Bin works for both AD DS and AD LDS environments.
A quick note about a deleted object’s lifetime: The value of an object’s tombstone lifetime is determined by the msDS-deletedObjectLifetime attribute. The recycled object lifetime is determined by the value of the legacy tombstoneLifetime attribute; by default, this value is null. This means that the deleted object lifetime is set to the value of the recycled object lifetime. By default, the recycled object lifetime, which is stored in the tombstoneLifetime attribute, also is null. This means that the recycled object lifetime defaults to 180 days. These two values can be modified at any time. When msDS-deletedObjectLife is set to some value other than null, it no longer assumes the value of tombstoneLifetime.
To modify these values, it is recommended to use Windows PowerShell. Here is an example of setting the tombstoneLifetime value to 365 days (all on one line):
Set-ADObject -Identity “CN=Directory Service,CN=Windows NT,CN=Services,CN=Configuration,DC=Adatum,DC=com” –Partition “CN=Configuration,DC=Adatum,DC=com” –Replace:@{“tombstoneLifetime” = 365}
Here is an example of setting the deleted object lifetime to 365 days (all on one line):
Set-ADObject -Identity “CN=Directory Service,CN=Windows NT,CN=Services,CN=Configuration,DC=Adatum,DC=com” –Partition “CN=Configuration,DC=Adatum,DC=com” –Replace:@{“msDS-DeletedObjectLifetime” = 365}
You can also configure these values by using the Ldp.exe tool.
To enable the Active Directory Recycle Bin in Windows Server 2012, you can do one of the following:
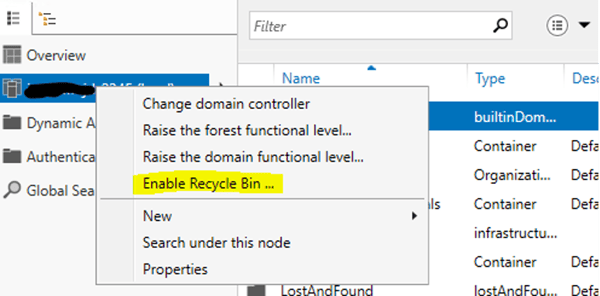
The Active Directory Recycle Bin needs to be enabled in order to restore deleted items with all their attributes. One last piece of critical information is that once you have enabled to Recycle Bin feature it cannot be disabled.
The Active Directory Administrative Center provides administrators with a graphical interface for restoring your deleted AD objects. After the Recycle Bin has been enabled, admins can actually see the Deleted Objects container in the navigation pane. Administrators can view the deleted objects in the container until the object lifetime has expired. Objects can either be restored back to their original location or to a new location within AD DS.
Not all restores need to be done from backup. Using tools like Ldp.exe and the Active Directory Recycle Bin can save you a lot of time restoring individual objects in AD DS. However, not all restores will be this easy. Active Directory Monitoring tools will not pick up on these accidents very easily. Most times these issues are found afterwards, and we need to fix them as soon as possible. You will want to search for event IDs:
In order for these events to be monitored, you will need to enable auditing of your domain controllers using group policy. The policies you will need to enable include:
In part two of this series, we will explore backup technologies, backup and recovery tools, and the AD DS backup and recovery process.
Active Directory is the foundation of your network, and the structure that controls access to the most critical resources in your organization. The ENow Active Directory Monitoring and Reporting tool uncovers cracks in your Active Directory that can cause a security breach or poor end-user experience and enables you to quickly identify and remove users that have inappropriate access to privileged groups (Schema Admins, Domain Administrators). While ENow is not an auditing software, our reports reduce the amount of work required to cover HIPAA, SOX, and other compliance audits.
Access your FREE 14-day trial to accelerate your security awareness and simplify your compliance audits. Includes entire library of reports.

Jonathan is an Information Technology consultant and instructor that specializes in migrations, security audits, new Microsoft technology implementations, and support contracts for Microsoft technologies. Jonathan also has expertise in Office 365 Services including, but not limited to, Azure Active Directory, Exchange Online, Skype for Business/Teams, SharePoint Online/OneDrive, Microsoft Azure/Office 365 Security and Compliance features including alerts, permissions, information classification, data loss prevention, information governance, threat management, data privacy, and reporting.


In Part 2 of this series, we'll discuss backup and recovery options for Active Directory Domain...


In the previous article we looked at the operations and processes regarding backup and recovery of...