Public Folder Scripts and Basic Authentication
By now you must be aware that Microsoft will turn off basic authentication in Office 365 later this...


Microsoft will stop support for basic authentication in Office 365 starting October 1, 2022. Uhm, that’s a week from the time of writing. That sounds scary, but Microsoft is already stopping basic authentication for tenants for quite some time, so chances are that it is already turned off for your organization.
Why is Microsoft turning off basic authentication? To improve security in Office 365. Basic authentication is a widely used attack vector and relatively easy to misuse. Modern Authentication is much more difficult to misuse, and it also offer additional services like multi-factor authentication.
Important to note: Microsoft is turning off basic authentication for all protocols used in Exchange Online. The protocols themselves are NOT turned off and continue to run, it is just the authentication method!
Microsoft is taking an aggressive approach on turning off basic authentication. The original plan was to start on October 1st and take three months to turn it off for everybody. Microsoft has changed their plan, basic authentication for all tenants in Office 365 will be turned off in just one month!
How do you check if modern authentication is enabled in your Office 365 tenant? In the Microsoft Online Portal (https://admin.microsoft.com), select Settings | Org Settings | Modern Authentication. The top box with “Turn on modern authentication for Outlook 2013 for Windows and later (recommended)” should be checked as shown in the following screenshot:
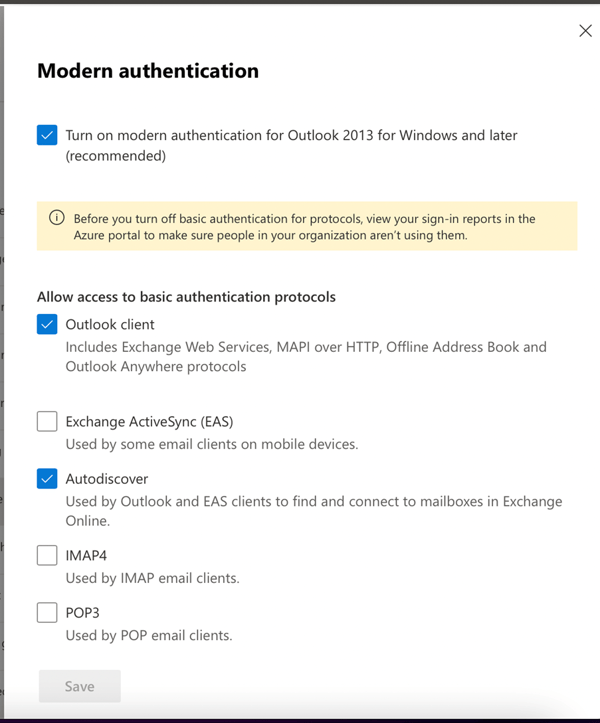
Other clients can be checked or unchecked, it depends a bit on your organization. If a box is checked it means that clients can use basic authentication. From what I have seen the last three years is that old Outlook 2010, unpatched Outlook 2013 clients (they are out there!), Android mail clients using Exchange ActiveSync and POP3/IMAP4 clients are using basic authentication extensively.
To find out if you have any clients in your organization using basic authentication, go to the Microsoft Azure Portal (https://portal.azure.com) and select the Azure AD tile. You can also navigate directly to the Azure AD portal via https://aad.portal.azure.com and scroll down to Sign-in logs under Monitoring. All logins are listed here so you must add a filter. Click the Add filters button and select the Client app button. Click on Client app: None Selected and select the legacy clients you want to check as shown in the following screenshot:
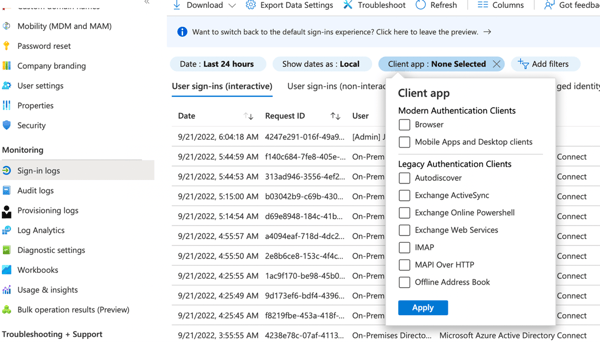
If there are any clients using basic authentication in your organization, they will show up here. If there are it is time to act.
First of all, make sure all your clients are able to use Modern Authentication or OAuth. Most operating systems are able to use OAuth so that should not be a problem. Email clients is a different story:
But do not underestimate this, it can take quite some time to do proper research in your organization to figure this one out!
When clients no longer use basic authentication, you can start disabling basic authentication. The easiest way is to create an authentication policy using PowerShell in Exchange Online using the New-AuthenticationPolicy.
To create a new authentication policy that will block basic authentication for Exchange ActiveSync, POP3 and IMAP4 you can use the following command:
[PS] C:\> New-AuthenticationPolicy -Name "Block Basic Auth" -BlockLegacyAuthActiveSync -BlockLegacyAuthPop -BlockLegacyAuthImap
The next step is to assign this policy to a user using the Set-User command, for example:
[PS] C:\> Set-User -Identity John@contoso.com -AuthenticationPolicy "Block Basic Auth"
Please be aware that it can take a lot of time before this authentication policy becomes active.
To remove this authentication policy from the user, just use the $NULL value for the -AuthenticationPolicy option:
[PS] C:\> Set-User -Identity John@contoso.com -AuthenticationPolicy $NULL
The good part of this approach you can do it gradually. Maybe I must say “you could have done this gradually” since Microsoft is going to start stopping basic authentication anytime soon in your environment so there’s not much time left I’m afraid.
Summary
Microsoft is going to disable basic authentication as of October 1, 2022 for all protocols except authenticated SMTP. They do this to improve security in Office 365 since basic authentication is a widely used attack vector.
You must check your environment to see if there are any clients using basic authentication these clients will no longer be able to login somewhere in October.
To prevent any nasty surprises and potentially overload your helpdesk with calls it is time for action. Use the steps in this article as a starting point to prepare and possibly disable basic authentication for your users.
For more in-depth information you can check two blog posts I wrote two and a half years ago:
https://jaapwesselius.com/2020/03/30/basic-authentication-in-office-365-part-i/
https://jaapwesselius.com/2020/03/31/basic-authentication-in-office-365-part-ii/
With email being one of the most mission-critical tools for organizations today, how do you ensure vital business communication stays up and running? How do you demonstrate to senior management that additional resources are needed to meet growing demand or that service levels are being met?
Developed by Exchange architects with direct product input from Exchange MVPs, ENow's Mailscape makes your job easier by putting everything you need into a single, concise OneLook dashboard, instead of forcing you to use fragmented and complicated tools for monitoring and reporting. Easy to deploy and intuitive to use, get started with Mailscape in minutes rather than days.
ACCESS YOUR FREE 14-DAY TRIAL and combine all key elements for your Exchange monitoring and reporting to keep your messaging infrastructure up and running like a pro!
PRODUCT HIGHLIGHTS


Jaap is a Microsoft MVP for Office Apps and Services. Jaap is an independent consultant, primarily focusing on Exchange server, Skype for Business and Office 365.


By now you must be aware that Microsoft will turn off basic authentication in Office 365 later this...

iOS – Changing from basic auth to modern auth connectivity on your Apple device. (To learn more...