Microsoft Service Incident MO1221364 on January 22, 2026
On January 22, 2026, a significant service incident began affecting Microsoft 365 users throughout...

On October 29, 2025, customers and Microsoft services that were leveraging Azure Front Door (AFD) experienced latencies, timeouts, and errors. Numerous downstream services were impacted.
Microsoft reported this outage on the Microsoft 365 Service Health Page as MO1181369.
On Wednesday, October 29, 2025, a major service incident affected Microsoft’s Azure cloud infrastructure, impacting Microsoft 365, its admin portals, and numerous downstream services. The incident, tracked under MO1181369 by Microsoft, was reported to the Azure Status page at 16:35 UTC (9:35 AM PT).
According to Microsoft’s notice, at approximately 16:00 UTC (9:00 AM PT), “Customers and Microsoft services leveraging Azure Front Door (AFD) may have experienced latencies, timeouts, and errors. Affected Azure services include, but are not limited to: App Service, Azure Active Directory B2C, Azure Communication Services, Azure Databricks, Azure Healthcare APIs, Azure Maps, Azure Portal, Azure SQL Database, Azure Virtual Desktop, Container Registry, Media Services, Microsoft Copilot for Security, Microsoft Defender External Attack Surface Management, Microsoft Entra ID (Mobility Management Policy Service, Identity & Access Management, and User Management (UX), Microsoft Purview, Microsoft Sentinel (Threat Intelligence), and Video Indexer.”
Subsequently, the Azure Support X account and Microsoft 365 Status X account acknowledged the issue and service disruption.
Per publicly available sources:
In ENow's Microsoft 365 Monitoring system, the first domino to fall was the Exchange Online OWA Logon synthetic transaction. This out-of-the-box test runs every few minutes to verify that the Outlook Web App is available.
We saw the first signs of latency anomalies around 8:30 AM PDT (≈15:30 UTC), when endpoint requests began to fail. Within about 30 minutes, the network endpoints were degraded. By the time the public status posts appeared on X (@MSFT365Status) and Microsoft’s portal, about an hour had passed. Our monitoring had already flagged abnormal behavior.
 Figure 1: @MSFT365Status Feed built into ENow Microsoft 365 Monitoring
Figure 1: @MSFT365Status Feed built into ENow Microsoft 365 Monitoring
 Figure 2: Service Health Page built into ENow Microsoft 365 Monitoring
Figure 2: Service Health Page built into ENow Microsoft 365 Monitoring
Here’s a breakdown of the detection flow. Because we monitor at multiple layers, our clients’ alerts triggered before most help‑desk tickets arrived).
ENow’s Synthetic transaction monitoring feature tests the ability for various workloads. In the case of this outage, Exchange Online OWA access was the first transaction to signal the failure.
 Figure 3: Exchange Online OWA Status Monitoring
Figure 3: Exchange Online OWA Status Monitoring
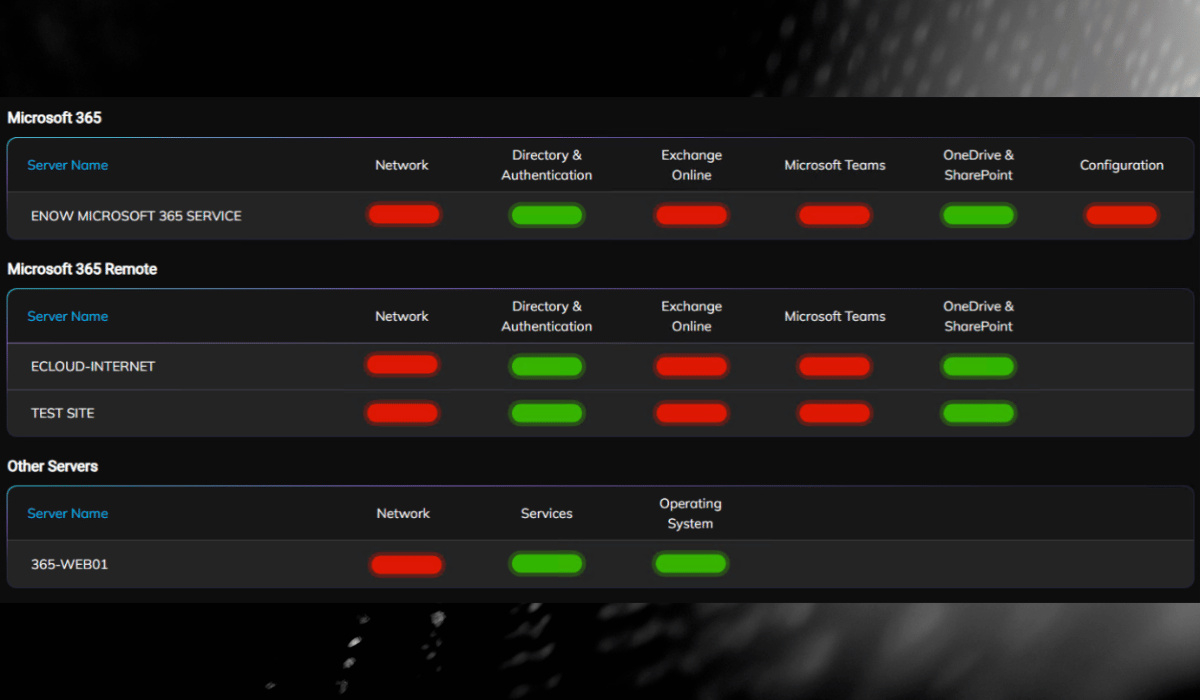
With ENow’s out-of-the-box network monitoring, we saw high latency with Microsoft’s Entra ID secure endpoints and eventual failures.
 Figure 4: Microsoft 365 Service Network Status Monitoring
Figure 4: Microsoft 365 Service Network Status Monitoring
 Figure 5: Azure Network Status Monitoring
Figure 5: Azure Network Status Monitoring
 Figure 6: Exchange Online Network Status
Figure 6: Exchange Online Network Status
 Figure 7: Microsoft Entra ID Network Status – monitored out of the box with ENow Monitoring for Microsoft.
Figure 7: Microsoft Entra ID Network Status – monitored out of the box with ENow Monitoring for Microsoft.
ENow’s Microsoft Monitoring tool allows Network Custom URLs to be monitored for availability and latency. Cloud App Security, Exchange Admin Center, Microsoft Purview, and Microsoft Security Intelligence portal all showed failures to connect.

Here are the top benefits of being ahead of the curve when a major outage happens:

Figure 9: Microsoft 365 SLA Status Monitoring
From our perspective, using this outage as a case study, here are some takeaways:
If you haven’t yet reviewed your monitoring & alerting posture for major cloud‑vendor services (Microsoft 365, Google Workspace, AWS, Azure etc.), now is a great moment. Here are some questions to ask:
The October 29 outage was a reminder: even giant cloud providers slip up, and when they do, the ripple effect can be massive. What sets well‑prepared IT teams apart is not “never failing” (that’s unrealistic) but detecting early and communicating well.
With ENow’s Microsoft Monitoring system in place, our Clients were able to detect the incident early, alert the right internal teams, draft user messaging, and minimize the secondary chaos that often follows such outages.
If your organization wants to convert that proactive posture into a competitive advantage (less downtime, better user trust, fewer escalations), then let’s talk about how your monitoring and communications workflow can be tuned for exactly these kinds of vendor‑cloud failures.
Effective outage communication and handling require real-time insights. ENow's proactive Microsoft 365 Monitoring provides enhanced visibility, resulting in faster issue resolution, reduced business impact, and increased user confidence in your IT team.
Learn about ENow's Microsoft 365 Monitoring and Reporting Platform, or contact us for a Microsoft 365 Monitoring Demo.

ENow protects and optimizes Microsoft 365, Copilot, and Entra ID, giving modern IT leaders clarity and simplicity to manage complex environments. From proactive monitoring to license optimization, adoption, and identity governance, ENow enables IT teams to manage, scale, and secure their Microsoft environment with confidence; all in one place, without the chaos.


On January 22, 2026, a significant service incident began affecting Microsoft 365 users throughout...


On Monday, June 5th, 2023, at approximately 10:50 AM (ET), Microsoft tweeted @MSFT365status that...