Using Defender for Cloud Apps to Control File downloads
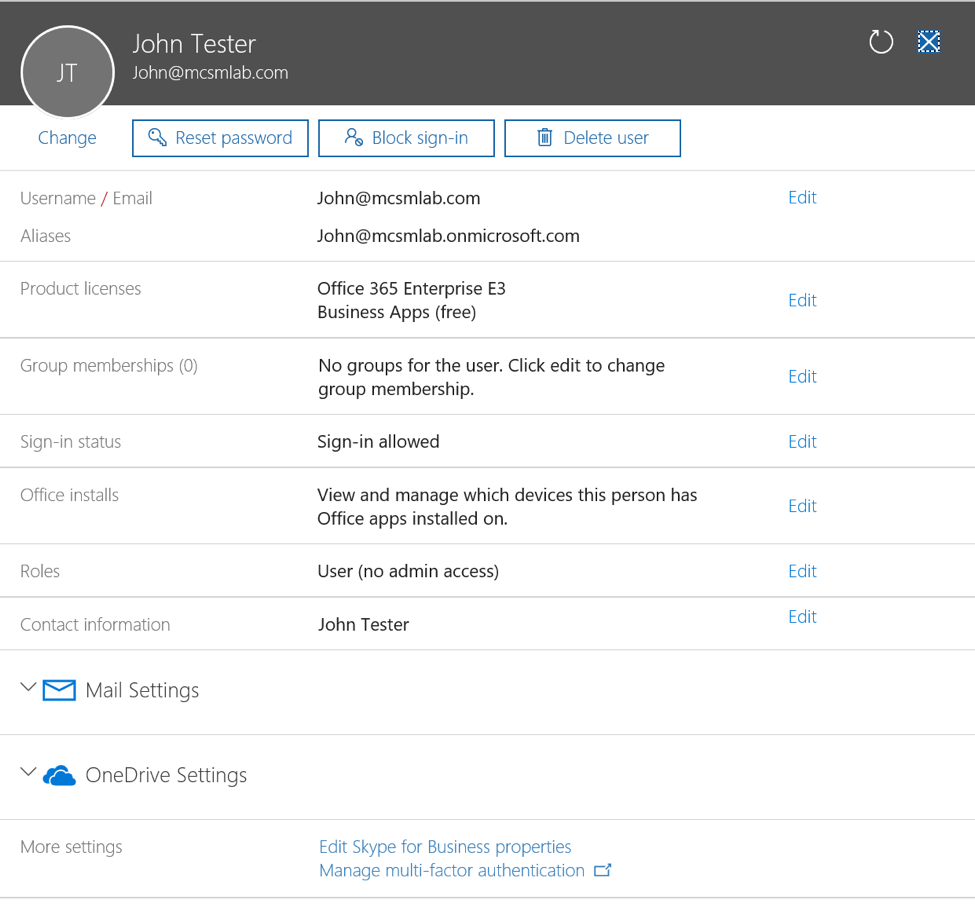
One situation I see often with customers is the desire to control and monitor file downloads from the cloud. For most organizations in most industries, it’s important to control your organization's data, and that data is often contained in files. The proprietary nature of information in files makes them very valuable to many organizations, and thusly important to control.