What Does “Supported” Mean to Microsoft?
There are a few words Microsoft likes to use in several different situations. “Federated” is a...

The value proposition for the services in the EM+S E5 suite does not seem like it has been convincing to customers for a while now. Over the last year or so, Microsoft has been putting a lot of work into the Defender services to improve that value proposition, and to provide a better technical security solution for Microsoft 365 customers.
In the last year or so Microsoft has rebranded and reorganized the Defender applications into Defender for Cloud Apps, Defender for Office 365, Defender for Endpoint, and Defender for Identity. While those four services are a good start, there are still gaps in the protection they provide.
To that end, Microsoft has added a new product in public preview to the Defender Suite, Microsoft Defender Vulnerability Management (DVM). DVM is targeted at improving vulnerability management in the following areas:
In this blog post we’re going to look at the public preview for this new service. How to get it activated in your tenant, what it does, and where I see it fitting into your overall security architecture for Microsoft 365.
While public previews for many new Microsoft 365 features are automatically added to tenants, the public preview for DVW requires a short process to activate. You can sign up here. That process only took me a couple of minutes, then I had new licenses in my tenant that I could assign to an admin account to gain access to DVM features. Once that is complete, you will have access to the feature we’ll cover below.
The GUI for the Microsoft 365 Defender stack of applications is mostly (but not entirely) homed in the Microsoft Security Portal. While this can make it a little difficult to differentiate the functionality of the different applications within the Defender stack, it also gives us a “one stop shop” for Microsoft 365 security configurations. Maybe a separate portal for each application would be a good idea, but then again maybe this way is best.
Once you have DVM licensed and you have logged into the Security Portal, you will find all the new DVM features accessible under the Endpoints section on the left-hand side of the screen:
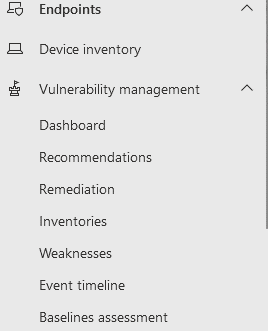
There are currently seven subsections under Vulnerability Management here. As this application is still in public preview, that may change before DVM hits GA.
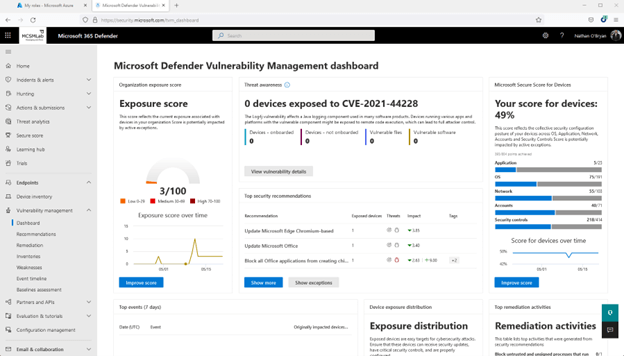
The first area to explore is the dashboard. Here you will find a quick view of a few different measures of vulnerability within your Microsoft 365 tenant.
In my tenant, you can see my exposure score is low (3/100 is a good thing. You want that number to be as low as possible), and my secure score for devices isn’t great (49% means I have remediated about half of the issues Microsoft monitors to make up that score).
Clicking on Improve Score on either of those widgets will take you to the recommendations sub-section, where suggested remediations are detailed to help you improve the security posture of your tenant.
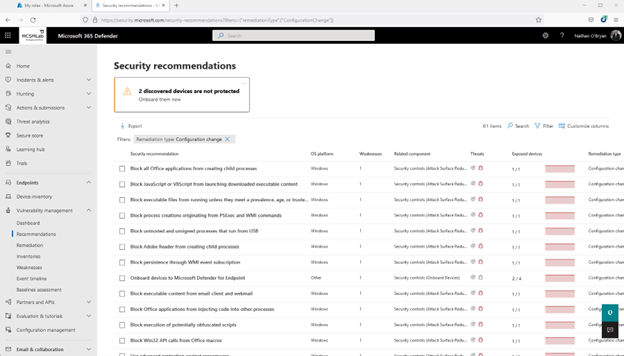
Below is a screenshot of the recommendations page for my device secure score. With 61 items to address, it seems like I have to some work to do in my tenant.
The remediation sub-section is for organizing the recommendations into active tasks.
Going back up to recommendations for my secure score for devices, I selected one of the recommendations (in this case “Update Office”), and then selected the Request remediation button at the bottom of the fly-out page.
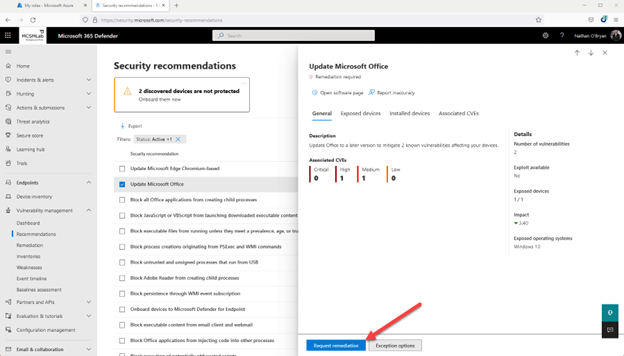
This will give you a quick wizard that allows you to mark that recommendation for remediation. It’s by no means a full-blown ticketing system, but this looks like it could be helpful for prioritizing the implementation of those recommendations in your team. Not super helpful for me, as I am the only administrator in my tenant.
The inventories tab gives you an inventory of the applications, browser extensions, and certificates installed on Windows machines that have been inventoried into Endpoint Management.
I do have an iPad that has Defender, but no applications from that device are inventoried here. This sub-section will inventory macOS, Linux, and Windows. iOS and Android devices are left out for now.
The weaknesses sub-section is yet another view of the same information presented in a different way. Here you’ll see vulnerabilities that can affect your devices listed by vulnerability name.
Below you can see I selected one of the vulnerabilities that is related to Office. It shows me that I have one Windows 10 laptop that needs an Office update.
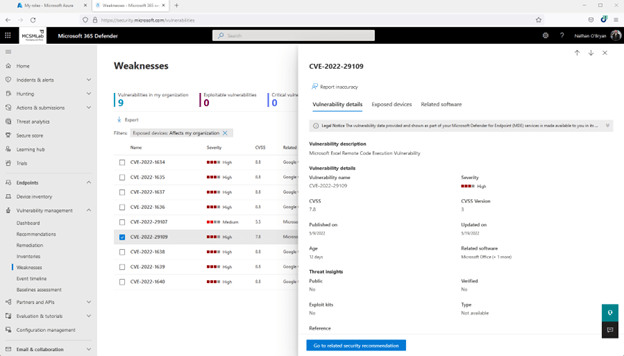
It’s telling me that updating Office on that one laptop will take care of the Recommendation, the Remediation that I opened from that Recommendation, and this Weakness listed here.
While that level of redundancy probably isn’t necessary for a small tenant like mine, I do look forward to playing around with DVM in a much larger tenant. I think this information would be much more useful in a larger environment where it’s more difficult to keep track of the different vulnerabilities affecting a deployment.
Guess what’s in the Event Timeline sub-section. If you guessed another view of the same vulnerabilities, then you just earned a gold star for the day.
In the screenshot below, you can see that I really need to update Office on that laptop!
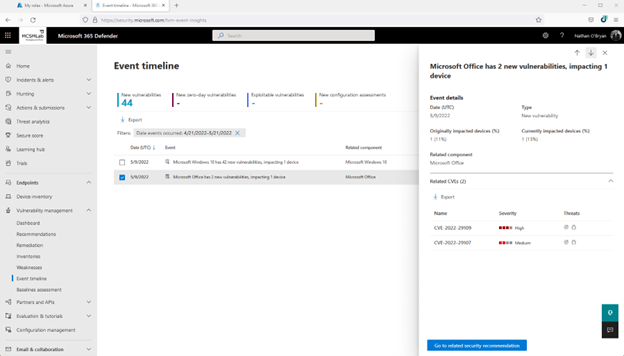
Again, this is the same two Office vulnerabilities that are shown in a slightly different view. There is even a button here that will take you back up to the Recommendations for these vulnerabilities.
So far DVM has shown us a dashboard that summarizes the vulnerabilities listed in the next five sub-sections, then those same vulnerabilities listed in those five different subsections. I don’t want to sound too “complainy” here, as this is good vulnerability information that can absolutely help administrators better secure their devices, but I do think those sub-sections could be condensed into a single pane with some sort of different views. I am not a UI designer, so maybe there is a good reason Microsoft felt they needed all that real estate within the Security Center to present the same information multiple times.
The Baseline Assessment sub-section, however, does provide different functionality. According to Microsoft Documentation:
“A security baseline profile is a customized profile that you can create to assess and monitor endpoints in your organization against industry security benchmarks. When you create a security baseline profile, you're creating a template that consists of multiple device configuration settings and a base benchmark to compare against.”
To create a Baseline Assessment profile:
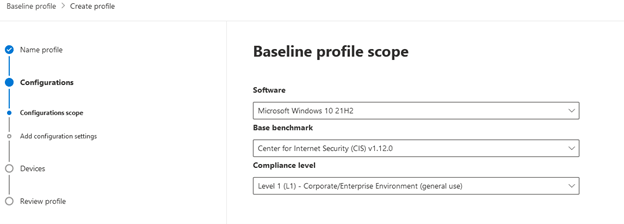
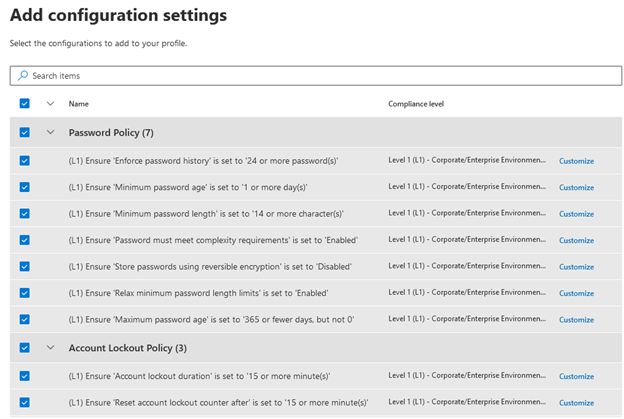
I’m going to let that run, then we’ll take a deeper look at the baseline assessment and over DVM features in a future blog post.
With email being one of the most mission-critical tools for organizations today, how do you ensure vital business communication stays up and running? How do you demonstrate to senior management that additional resources are needed to meet growing demand or that service levels are being met?
Developed by Exchange architects with direct product input from Exchange MVPs, ENow's Mailscape makes your job easier by putting everything you need into a single, concise OneLook dashboard, instead of forcing you to use fragmented and complicated tools for monitoring and reporting. Easy to deploy and intuitive to use, get started with Mailscape in minutes rather than days.
ACCESS YOUR FREE 14-DAY TRIAL and combine all key elements for your Exchange monitoring and reporting to keep your messaging infrastructure up and running like a pro!
PRODUCT HIGHLIGHTS


Nathan is a five time former Microsoft MVP and he specializes in Exchange, Microsoft 365, Active Directory, and cloud identity and security.


There are a few words Microsoft likes to use in several different situations. “Federated” is a...


As an Exchange admin you could not have missed it – The Microsoft Exchange Conference 2022. I have...