How to Build a SCCM OSD Progress Report to Wow Your Boss - Part 3
If you haven’t read part 1 and part 2 of this article series yet, we recommend you do. Reading parts 1 and 2 are essential for proceeding part 3.
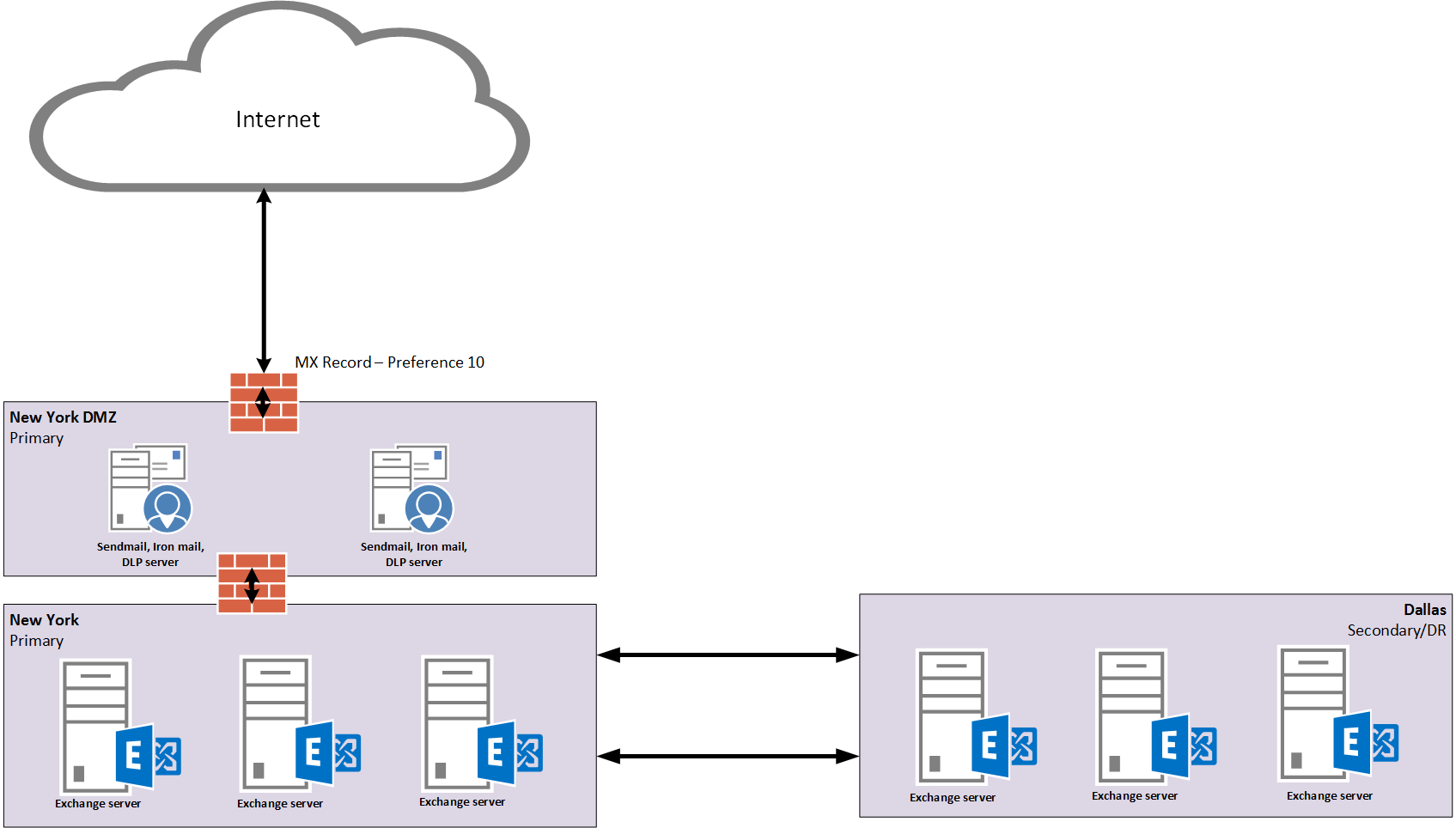
Moving past parts 1 and 2, I now have all my clients using my new inventory classes I created. I’ve verified with a few clients that they are successfully sending this data to the site server. What’s next? The next piece of this process is to query the database, however this is an optional step. What we'll discuss next is setting up the SSRS report, but I always like to setup a SQL query in the SCCM console first. It’s a quick and easy way to figure out what’s in your database.