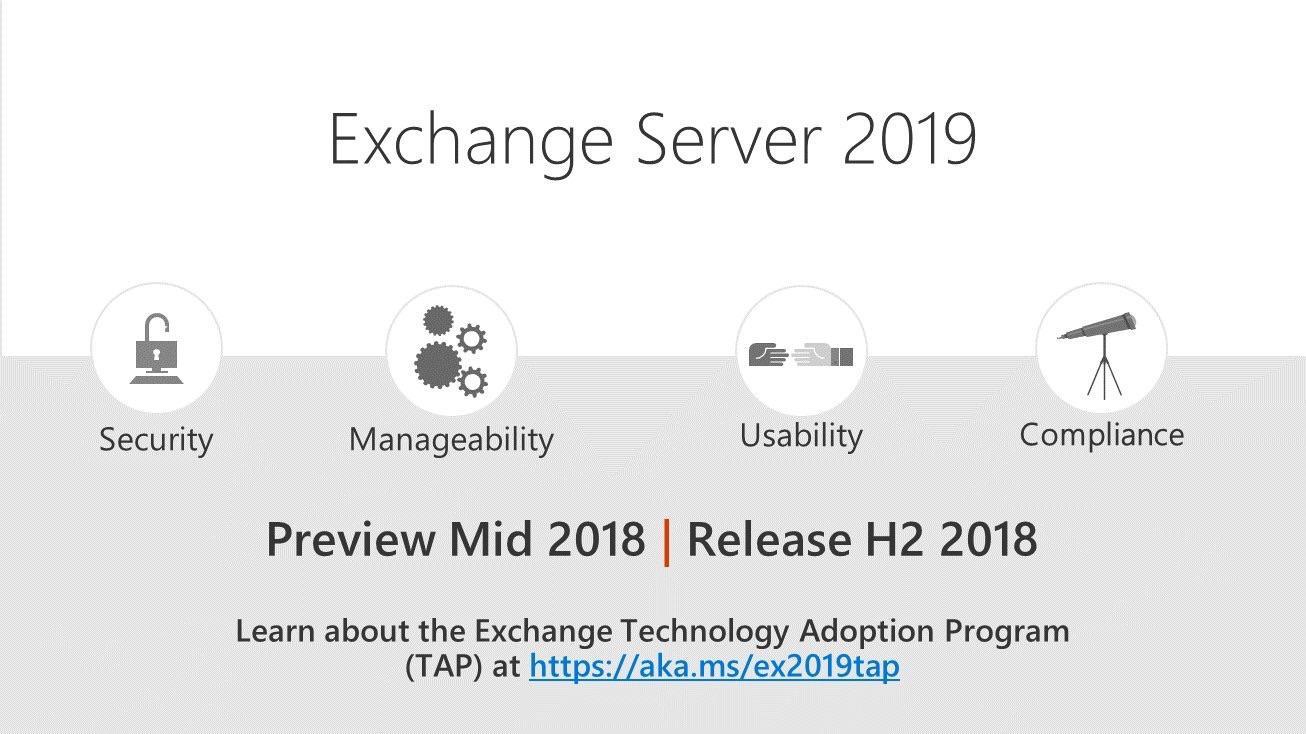
This time next year we’ll (hopefully) be in the midst of project planning for the newly released Exchange Server 2019. After a scheduled late-2018 release, many organizations will be looking to learn, test, deploy, and administer the new on-premises Exchange version after returning from their holiday break. As someone who works in the Exchange Support and Consulting world, this (Jan 2017) is actually a relatively slow period for us. Exchange 2016 has been released for a couple years, its bugs and quirks mitigated, and the rush of early adopter migrations have passed; leaving only the steady flow of migration and deployment work driven by company financial scheduling rather than the Exchange product release cycle.